[ad_1]
Ransomware and other malware-based attacks continue to make headlines, but that doesn’t mean they deserve all the attention. Another threat security teams need to be aware of is user enumeration attacks.
What is an enumeration attack?
Enumeration attacks happen when malicious actors brute-force access to web applications. Attackers often use credentials exposed in previous breaches or social engineering scams to attempt access to other websites and applications where users may have used the same login information.
If successful, attackers may gain access to personally identifiable information (PII) of customers and employees. They can then sell the PII on the dark web or use it to attack their victims, for example, by draining their bank accounts or making charges on their credit cards.
How does an enumeration attack work?
The majority of enumeration attacks target the databases of web-based applications. Such attacks most often occur on the app’s main login page.
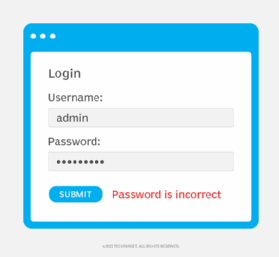
When conducting an enumeration attack on a login page, attackers observe how the web application reacts to a brute-force entry attempt:
- If the reaction is a “username not found” message, attackers know the username isn’t in that particular database.
- If the reaction is a “password is incorrect” message, attackers know the username exists within the database and that they can continue to brute-force attack that application.
- If the reaction is a “username and/or password not found” message, attackers are unsure which credential is correct, if either.
Enumeration attacks can also be conducted against “forgot password” and “forgot username” forms in applications.
How to prevent enumeration attacks
While it’s not possible to 100% prevent user enumeration attacks, organizations should take the following steps to make them more difficult:
- Employ cryptic wording. Well-developed login pages should display a “username and/or password not valid” message. This makes it difficult for attackers to know if the username, password or both are incorrect.
- Use a next-generation firewall (NGFW). While all firewalls block traffic based on established rules, NGFWs in particular can limit the number of failed login attempts from multiple IP addresses.

Use CAPTCHA to prevent bots from logging in to user accounts.
- Use a web application firewall (WAF). WAFs filter HTTP traffic for malicious or rogue traffic incoming from the internet.
- Use CAPTCHA. CAPTCHA not only limits the number of times a person can attempt to log in to an app, but also helps slow down attacks and eliminate bots. CAPTCHA can also block automated enumeration attacks.
- Implement multifactor authentication (MFA). MFA, which requires additional credentials to successfully log in to an account, blocks cyber attackers from exploiting server responses used to launch enumeration attacks because they are unable to log in without the additional credential(s).
- Secure source code. The best way to mitigate the risk of an enumeration attack comes down to securing the source code of the web application. Make sure any source code — open source or otherwise — is updated and tested through DevSecOps methods before being implemented in production environments.
This was last published in December 2022
Dig Deeper on Threats and vulnerabilities
[ad_2]
Read More: news.google.com










 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  USDC
USDC  TRON
TRON  Dogecoin
Dogecoin  Lido Staked Ether
Lido Staked Ether  Cardano
Cardano  Wrapped Bitcoin
Wrapped Bitcoin  Hyperliquid
Hyperliquid  Wrapped stETH
Wrapped stETH  Sui
Sui  Bitcoin Cash
Bitcoin Cash  LEO Token
LEO Token  Chainlink
Chainlink  Stellar
Stellar  Avalanche
Avalanche  Toncoin
Toncoin  USDS
USDS  WhiteBIT Coin
WhiteBIT Coin  Shiba Inu
Shiba Inu  WETH
WETH  Wrapped eETH
Wrapped eETH  Litecoin
Litecoin  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Hedera
Hedera  Ethena USDe
Ethena USDe  Monero
Monero  Polkadot
Polkadot  Bitget Token
Bitget Token  Coinbase Wrapped BTC
Coinbase Wrapped BTC  Uniswap
Uniswap  Pepe
Pepe  Pi Network
Pi Network  Aave
Aave  Dai
Dai  Ethena Staked USDe
Ethena Staked USDe  Bittensor
Bittensor  OKB
OKB  BlackRock USD Institutional Digital Liquidity Fund
BlackRock USD Institutional Digital Liquidity Fund  Aptos
Aptos  Internet Computer
Internet Computer  Cronos
Cronos  NEAR Protocol
NEAR Protocol  Jito Staked SOL
Jito Staked SOL  sUSDS
sUSDS  Ethereum Classic
Ethereum Classic