Han Sahin, CEO of ThreatFabric, explains why financial institutions should avoid investing in a ‘silver bullet’ solution to fight and prevent fraud, and offers advice on how to protect against future attacks
Fighting fraud can easily turn into a cat & mouse with fraudsters. The common approach in the industry is a reactive one: new threat, new mitigation tactic. Even if fraud facts prove otherwise, we still tend to rely on a silver bullet solution. There are three issues with this approach:
-
Fraudsters are usually more agile: They operate in smaller groups, they take time to explore unnoticed gaps & backdoors, and they usually play the first move.
-
We can only stop yesterday’s fraud: Reacting to escalating fraud means that we do not focus on the fraud risks of tomorrow.
-
We tend to rely on ‘proven’ technology: Modern technology like 2FA or biometric authentication can give a false sense of security, and we should assume that fraudsters will find their way around it.
Clients (usually banks) contact us when they get overwhelmed by a certain fraud type or when they cannot explain certain fraud numbers. We often remind our clients that stopping fraud is not about stopping fraud – it’s an organisational challenge focused on collecting enough relevant fraud risk indicators to reveal suspicious activities before the actual fraud attempt. Fighting fraud is about proactivity and about ensuring peace of mind during any fraud wave.
So which fraud risk indicators are relevant? This question can only be answered if you fully understand your organisation’s specific threat landscape. It is easy to assume that we should focus on the most lucrative fraud variants first, like Authorised Push Payment (APP) fraud: around GBP 250 million was lost to this in H1 2022 alone according to UK Finance. But then we are playing the cat & mouse game again. As mentioned before, fraudsters are more agile than banks, so they are already preparing for the moment that APP fraud is not lucrative anymore. We should prepare for their next move.
Our fraud research – which includes darknet intelligence – shows that upcoming campaigns for 2023 are often based on Device Takeover (DTO) fraud, ATS attacks (like SharkBot), and other fraud variants driven by banking malware or Remote Access Tools (RATs) – often in a sophisticated hybrid combination with classic APP attack patterns. Banking malware is part of so-called ‘dropper apps’: fully functional normal apps that are available through various channels, including the official Google Play Store. We cannot expect banking customers to recognise these highly obfuscated malicious apps. Moreover, new sectors & providers are being targeted. The top-5 of most targeted apps are crypto wallets, as they often don’t have the strict regulation, KYC checks, and fraud controls and experience that banks have gained dealing with fraudsters over decades. The upcoming BNPL providers are also notably vulnerable.
Once banks have invested in certain technology to protect themselves against fraud, they tend to rely on it without continuously validating the implementation or protecting against the ever-changing fraud landscape. This creates a false sense of security, because even technology or platforms that seemed waterproof for a while, often get compromised by fraud actors at a certain stage. This includes:
-
Two-Factor Authentication: Once banking malware runs on a (mobile) device, the second factor – whether it comes from SMS or a dedicated 2FA app – is fully compromised because they are automatically stolen using key logging or screen capturing mechanisms.
-
Biometric Authentication: Modern password-less solutions like face detection or fingerprint detection are highly reliable. However, the fallback mechanism for biometric authentication – entering your passcode – remains available for usability reasons, so that users can still access their devices when they are in the dark or have injured fingers. This is currently abused by Android banking trojans at a large scale: malware actively downgrades biometric authentication to password-based authentication and then steals the entered credentials. This is combined with fully automated scripts to commit the fraud itself (so-called ‘Automated Transfer System attacks’).
-
Official App Stores: The official app stores from Google and Apple contain apps with banking malware. Although many malicious apps get caught in the screening process, the most sophisticated ones make it through and get installed on end-user devices. Once the banking malware is installed, the end-user device is fully compromised and its owner is at high risk of becoming the next fraud victim.
So how can you protect yourself against these future attacks? First and foremost: do not gamble by investing in a ‘silver bullet’ solution – opting for a single solution is not agile at all and is therefore a risk in itself. Fraudsters can and will find a way around it. Expect high agility of fraudsters: If tactic A on channel 1 doesn’t work, they’ll go for tactic B on channel 2. Detecting fraud starts with expecting fraud, to create a mindset that focuses on tomorrow’s fraud. Modern fraud strategies and processes are holistic, layered, and omnichannel by nature. They focus on what all fraud and fraudster behaviour have in common. One thing that all fraud has in common is that a certain amount of preparation is needed from the attacker’s side. Whether it’s stealing credentials or making a victim believe he’s talking to a bank: it’s all preparation for the actual fraud, and it’s detectable.
These early fraud risk indicators are often visible on a device or behavioural level. The earlier the fraud risk indicator, the better. Some fraud risk indicators – for example, those for detecting APP fraud – are visible months before the first fraud attempt takes place:
-
Detect fraudster behaviour: Convince people to install a malicious app, log into a bank account, remote control of banking app, bypassing authentication, etc.
-
Detect fraudster tools: RATs, banking malware, on-call detection, etc.

Transaction monitoring is popular nowadays, but ultimately it is reactive by nature as well as a single-point solution with limited visibility. That said, it can be powerful for validating fraud, if enriched with early fraud risk indicators from a device and behavioural level:
-
Add context and details, including continuous authentication and trust scoring.
-
Less false positives and better alert prioritisation.
-
Insight into risks and how fraudsters operate, even if the fraud attempt doesn’t take place: you generate your own intelligence.
So, what could you do now? A few tips:
-
Don’t try to win the fight alone: Collaborate as fraudsters do, but in our case with your peers, other banks, solution providers, and fraud communities such as UK Finance or About-Fraud.
-
Evaluate if your fraud and KYC strategy is ready for tomorrow’s fraud.
-
Invest in omnichannel device-level visibility to enrich your fraud scoring engine and transaction monitoring.
-
Invest in specific rather than generic fraud intelligence: Which threats are targeting your organisation and country – and what is the exact modus operandi behind them?
If you require any assistance or details insights, do not hesitate to contact us at info@threatfabric.com
About Han Sahin
 Han is the co-founder and CEO of ThreatFabric. He is a renowned fraud fighter and visionary, with over a decade of experience in threat intelligence and online fraud detection. Han previously worked in banks and is an experienced cyber entrepreneur, having co-founded Securify which was successfully sold to Solvinity in 2021.
Han is the co-founder and CEO of ThreatFabric. He is a renowned fraud fighter and visionary, with over a decade of experience in threat intelligence and online fraud detection. Han previously worked in banks and is an experienced cyber entrepreneur, having co-founded Securify which was successfully sold to Solvinity in 2021.
About ThreatFabric
 Founded in 2015 and headquartered in Amsterdam, ThreatFabric is a fast-growing fraud company and one of Europe’s thought leaders in online fraud detection and intelligence. ThreatFabric’s Fraud Risk Suite enables safe & frictionless payment journeys by integrating industry-leading threat intelligence, behavioural analytics, advanced device fingerprinting, and 10.000+ adaptive fraud indicators.
Founded in 2015 and headquartered in Amsterdam, ThreatFabric is a fast-growing fraud company and one of Europe’s thought leaders in online fraud detection and intelligence. ThreatFabric’s Fraud Risk Suite enables safe & frictionless payment journeys by integrating industry-leading threat intelligence, behavioural analytics, advanced device fingerprinting, and 10.000+ adaptive fraud indicators.
Read More: news.google.com





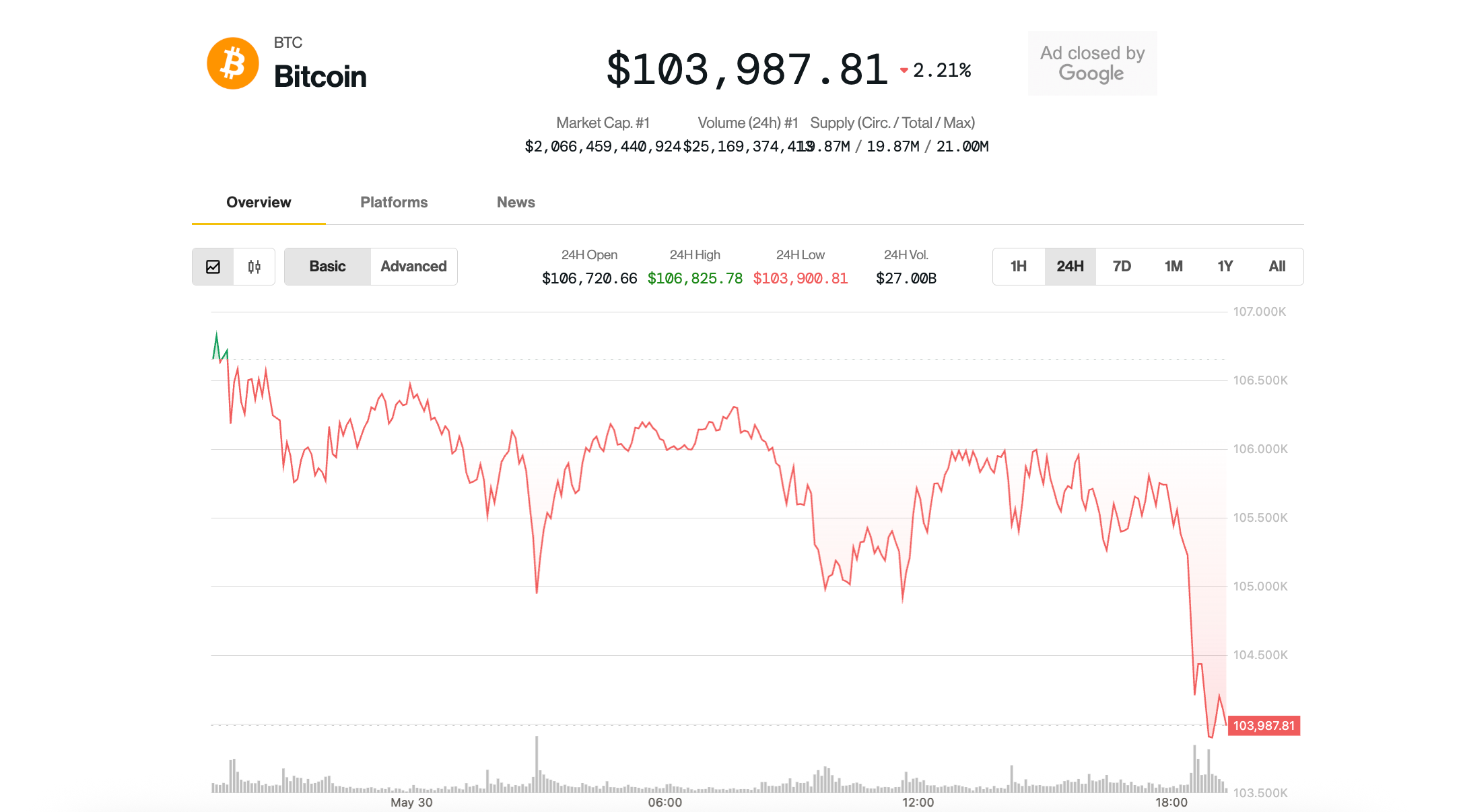


 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  USDC
USDC  Dogecoin
Dogecoin  TRON
TRON  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  Wrapped Bitcoin
Wrapped Bitcoin  Wrapped stETH
Wrapped stETH  Sui
Sui  Hyperliquid
Hyperliquid  Chainlink
Chainlink  Avalanche
Avalanche  Stellar
Stellar  LEO Token
LEO Token  Bitcoin Cash
Bitcoin Cash  Toncoin
Toncoin  Shiba Inu
Shiba Inu  USDS
USDS  Hedera
Hedera  WETH
WETH  Wrapped eETH
Wrapped eETH  Litecoin
Litecoin  Polkadot
Polkadot  Monero
Monero  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Bitget Token
Bitget Token  Ethena USDe
Ethena USDe  Pepe
Pepe  WhiteBIT Coin
WhiteBIT Coin  Pi Network
Pi Network  Coinbase Wrapped BTC
Coinbase Wrapped BTC  Dai
Dai  Aave
Aave  Uniswap
Uniswap  Bittensor
Bittensor  Cronos
Cronos  OKB
OKB  Ethena Staked USDe
Ethena Staked USDe  Jito Staked SOL
Jito Staked SOL  NEAR Protocol
NEAR Protocol  Aptos
Aptos  BlackRock USD Institutional Digital Liquidity Fund
BlackRock USD Institutional Digital Liquidity Fund  Tokenize Xchange
Tokenize Xchange  Ondo
Ondo  Ethereum Classic
Ethereum Classic