A nefarious character is demanding Optus pay US$1 million (A$1.5 million) in cryptocurrency otherwise they will leak sensitive information about millions of Australians that they claim to have obtained in a sophisticated hack.
The ransom demand appeared on a forum early on Saturday morning and experts say so far it appears legitimate.
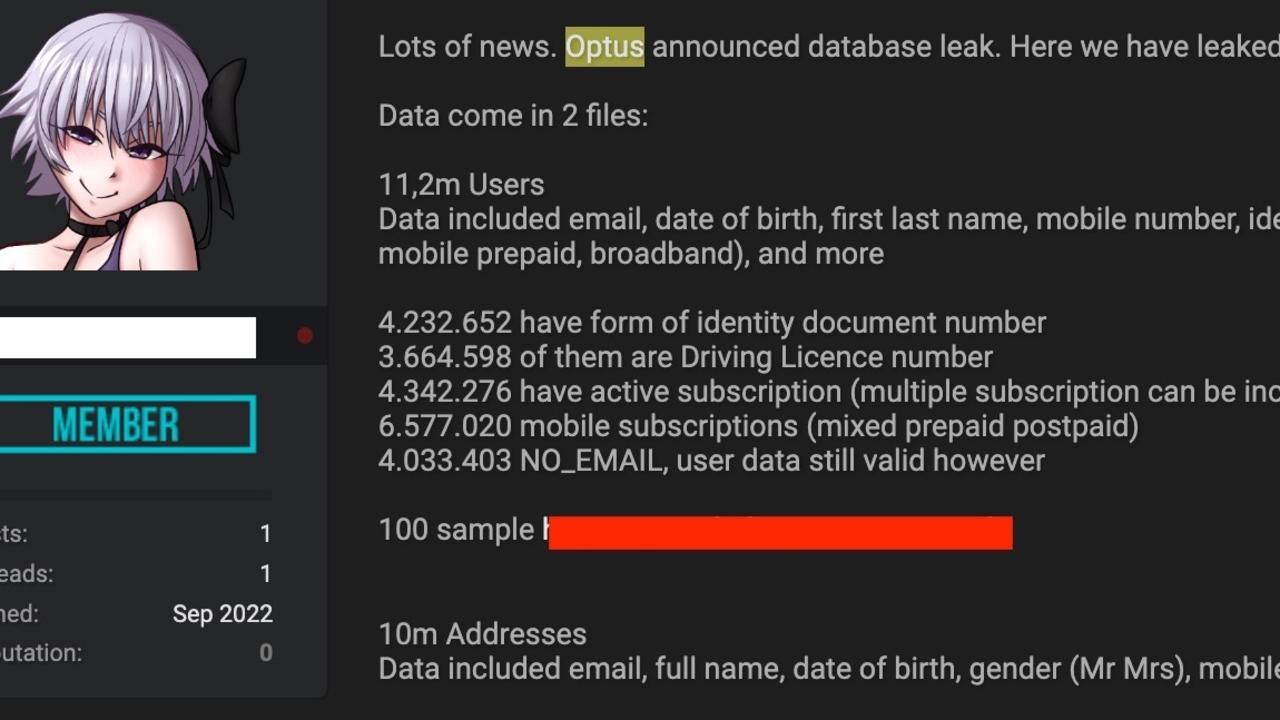
The so-called hacker claims to have important data about 11.2 million Optus customers, including their names, dates of birth, phone numbers, email addresses, and, for a subset of customers, addresses and ID document numbers such as driver’s licence or passport numbers.
“Optus if you are reading! price for us to not sale data is 1.000.000$US We give you 1 week to decide,” part of their message reads on the forum.
The hacker showed a sample of the dataset to prove their authenticity, which cyber security researcher and writer Jeremy Kirk from ISMG Corp said aligned with the breach and indicated they may indeed be the person behind the breach.
“I just ran 13 email addresses from the first batch of sample data from the alleged Optus leak through Haveibeenpwned [a website that shows if your email or phone number has been involved in a breach]. Six come back as unique (not in another breach indexed in HIBP).
“Again, another strong sign that the Optus data is real,” he wrote on Twitter.
Mr Kirk also said he contacted the hacker and they gave him a detailed explanation on how they completed the hack, which also convinced him the person was “the real deal”.
The cyber criminal wants the payment to be made in Monero, a decentralised cryptocurrency, making it hard to track down the identity of the recipient.
On Thursday, Optus revealed the data of 9.8 million Australians had been breached and the following morning the company’s CEO, Kelly Bayer Rosmarin, made an emotional apology.
The alleged hacker claims that Optus has a week to respond otherwise they will sell the data elsewhere.
Optus has not confirmed if it is aware of the ransom demand or whether it is indeed legitimate.
In a statement, the telco company said it cannot comment while the matter is under police investigation. They did not answer news.com.au’s question about whether they intended to pay the ransom.
The Australian Federal Police said in a statement to news.com.au on Sunday morning that they had come across the person taking credit for the Optus cyber attack and were closely monitoring it.
“The AFP is aware of reports alleging stolen Optus customer data and credentials may be being sold through a number of forums, including the dark web,” an AFP spokesman said in a statement.
“The AFP is using specialist capability to monitor the dark web and other technologies, and will not hesitate to take action against those who are breaking the law.”
The spokesman also said buying stolen credentials was a crime that could land the offender up to 10 years in prison.
There is no guarantee that the cyber criminal will protect the data even if the ransom is paid.
However, an ABC investigation from last year found that big corporations are forking out millions of dollars a year in ransom money to protect sensitive information in what they said was an “open secret” in the business world.
Over the last two years, some significant breaches in Australia occurred at logistics company Toll Holdings, meat supplier JBS Foods and Nine Entertainment.
Mr Kirk said he tried to verify the data further by contacting some of the people whose data had been leaked in the sample released online.
Coincidentally, he said one of his neighbours was on the list.
“I found the person in the dataset. She was working in her front yard. She wants to stay unnamed but confirmed she is a former Optus customer and that her data is accurate. We still need a confirm from Optus on the data but this is all lining up,” he said.
Mr Kirk added: “She said it was kind of scary. She hadn’t been contacted by Optus yet.”
Optus has copped criticism for its handling of the breach, especially by contacting media and not customers directly.
The telco company said it would send “proactive personal notifications” to customers they thought have a “heightened risk” of being involved in the hack.
The company said it will not send any links in emails or SMS messages, in case cyber criminals try to impersonate Optus coaxing customers to click on dodgy web addresses.
It was initially thought that 9.8 million Australians had had their data stolen in an “absolute worst case scenario”.
Nearly 2.8 million customers had all of their details taken in the attack and about seven million had information like their dates of birth, email addresses and phone numbers taken by the hackers, initial reports claimed.
However, if this hacker is real, then it appears that a further two million accounts have been compromised, bringing the number to a total of 11.2 million.
The breaches date as far back as 2017.
It was also suggested that the data breach could be the result of “human error” after a programmer made a mistake, making the Optus system vulnerable to hackers.
A “senior insider” said an error made by a programmer may have opened the door for hackers.
“(It’s) still under investigation. However, this breach, like most, appears to come down to human error,” the source said.
They claimed programmers were attempting to open up Optus’ customer identity database to other systems via an application programming interface.
While it was believed the process would only grant access to authorised company systems, outsiders may have been granted access via a test network.
Indeed, the alleged hacker told Mr Kirk when asked how they had carried out the cyber attack: “No authenticate needed. That is bad access control. All open to internet for any one to use.”
If you have been impacted by the Optus data breach, email alex.turner-cohen@news.com.au.
Read More: www.news.com.au








 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  USDC
USDC  Solana
Solana  TRON
TRON  Dogecoin
Dogecoin  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  Wrapped Bitcoin
Wrapped Bitcoin  LEO Token
LEO Token  USDS
USDS  Chainlink
Chainlink  Avalanche
Avalanche  Toncoin
Toncoin  Hedera
Hedera  Stellar
Stellar  Shiba Inu
Shiba Inu  Sui
Sui  Wrapped stETH
Wrapped stETH  MANTRA
MANTRA  Bitcoin Cash
Bitcoin Cash  Litecoin
Litecoin  Polkadot
Polkadot  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Ethena USDe
Ethena USDe  Bitget Token
Bitget Token  Hyperliquid
Hyperliquid  WETH
WETH  WhiteBIT Coin
WhiteBIT Coin  Pi Network
Pi Network  Monero
Monero  Wrapped eETH
Wrapped eETH  Dai
Dai  OKB
OKB  sUSDS
sUSDS  Uniswap
Uniswap  Pepe
Pepe  Coinbase Wrapped BTC
Coinbase Wrapped BTC  Aptos
Aptos  Gate
Gate  Ondo
Ondo  Tokenize Xchange
Tokenize Xchange  NEAR Protocol
NEAR Protocol  Cronos
Cronos  Internet Computer
Internet Computer  Mantle
Mantle  Ethereum Classic
Ethereum Classic