Following on from the previous article that covered the on-chain identity landscape, this piece goes into detail around one specific category and taking a deeper look at what it entails. This piece will be focused around Web3 social and how it works. Let’s get into it.
The social category is one of the more exciting categories given the flurry of activity occurring in it and the tangibility of the use case for most people. From my perspective, these on-chain identity social projects aim to tap into the same idea:
This goal comes from the two decades of centralised social media companies having all their data and social graphs closed source, which prevents users from customising the experience of they would like to consume media limited or controversial. By having the social graph open, social media can become a lot more of “choose your adventure”.
All of the projects achieve this goal with different design philosophies but more or less converge to the same ideas. They all have the same concepts when you dig underneath the hood but with different names for them (or more ideas split up).
In order to make these social graphs open, there’s typically two paths that are pursued:
-
Do everything on-chain through minting NFTs or interacting with smart contracts
-
Do everything off-chain but still achieve the same intention
-
A mix of the above depending on the specific use case
Within this domain there are three core types of players that can emerge, sometimes one project aims to do all or certain bits selectively.
-
Protocol. This is the base where everything is built ground up from. These social protocols mimic the data structures of existing social networks to enable similar social experiences.
-
Middleware. These enhance the underlying protocols to offer functionality they may not have but users would like or that can enhance the experience.
-
Application. They leverage the protocols and the middleware to create some sort of client side software that allows users to interact in a user friendly interface.
Now given the recency of this category, the protocols are attempting to do all 3 in order to bootstrap the initial network. It doesn’t seem like the intention of any on-chain social apps is to be only vertically integrated in all 3 as it reduces the probabilities of developers building on top. However, an application needs to be built so that user generated content can exist and thrive.
Moving onto the protocols and how they’re structured, they all more or less follow the same structure in terms of the entities that exist. Below are the core components that all of them contain:
-
Profiles
-
These are your classic social media concepts of a profile that includes identifiable information about you. This will typically have some link to a web3 address so it can be used as another aspect of your on-chain identity.
-
-
Associations/Follows
-
Usually some indicator of your account finding interest in another profile on the network
-
-
Content
-
This can be different depending on what the social protocol is (ie: videos, posts, images)
-
-
Apps/Front-end
-
Some protocols will make it explicit which application is using the social graph where as others will have no idea of what consumes it.
-
Typically a design choice of the protocol itself
-
-
Governance/security/upgrades
-
How the protocol of the social graph is updated or secured
-
Various answers here and probably irrelevant for a long time until it isn’t
-
Now that you have a good primer on the general idea around this category, the next part of this article goes into the various projects and how they fit into this stack.
The first project that fits into this stack is Farcaster. Farcaster relies on the idea of Sufficient decentralization. This is a hybrid architecture with on-chain and off-chain components.
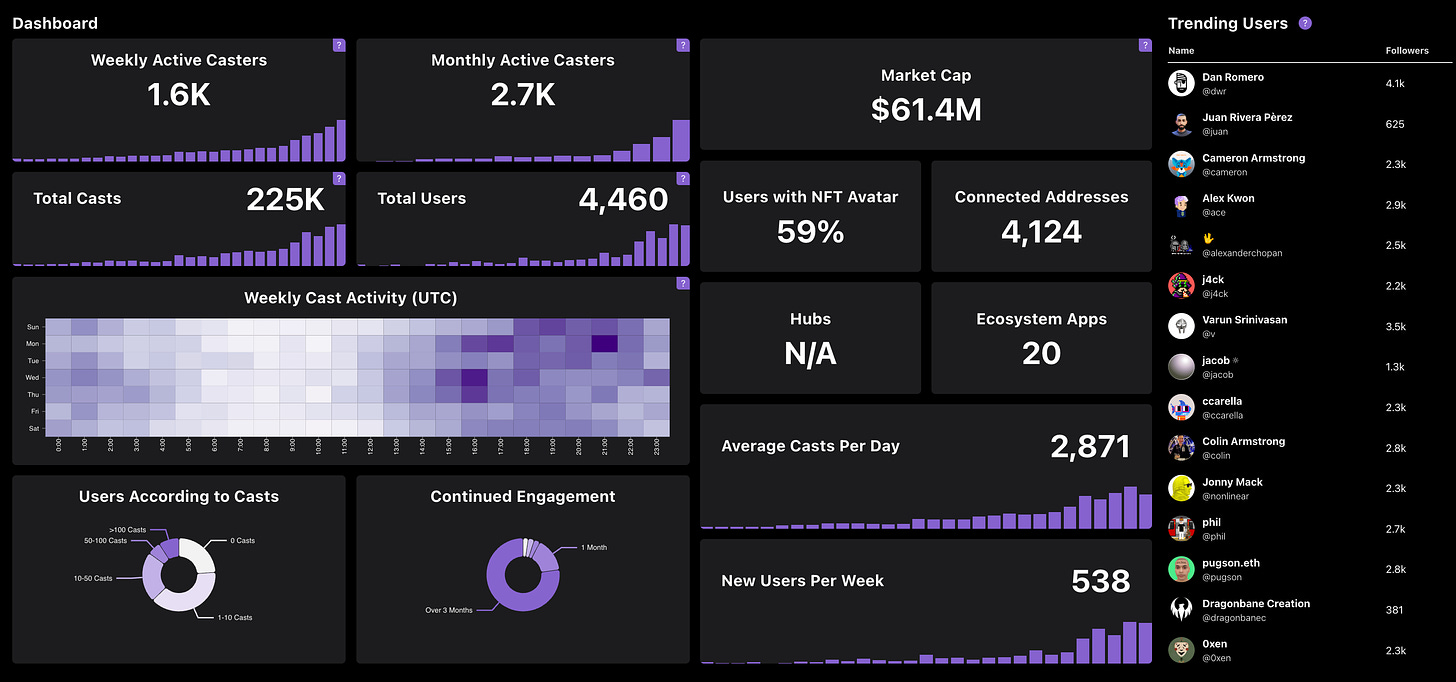
As we can see from the dashboard above, Farcaster is gaining traction week-on-week. With over 500 new users per week, 1600 weekly active casters, 4,124 connected addresses and a lot of continued engagement over 3 months.
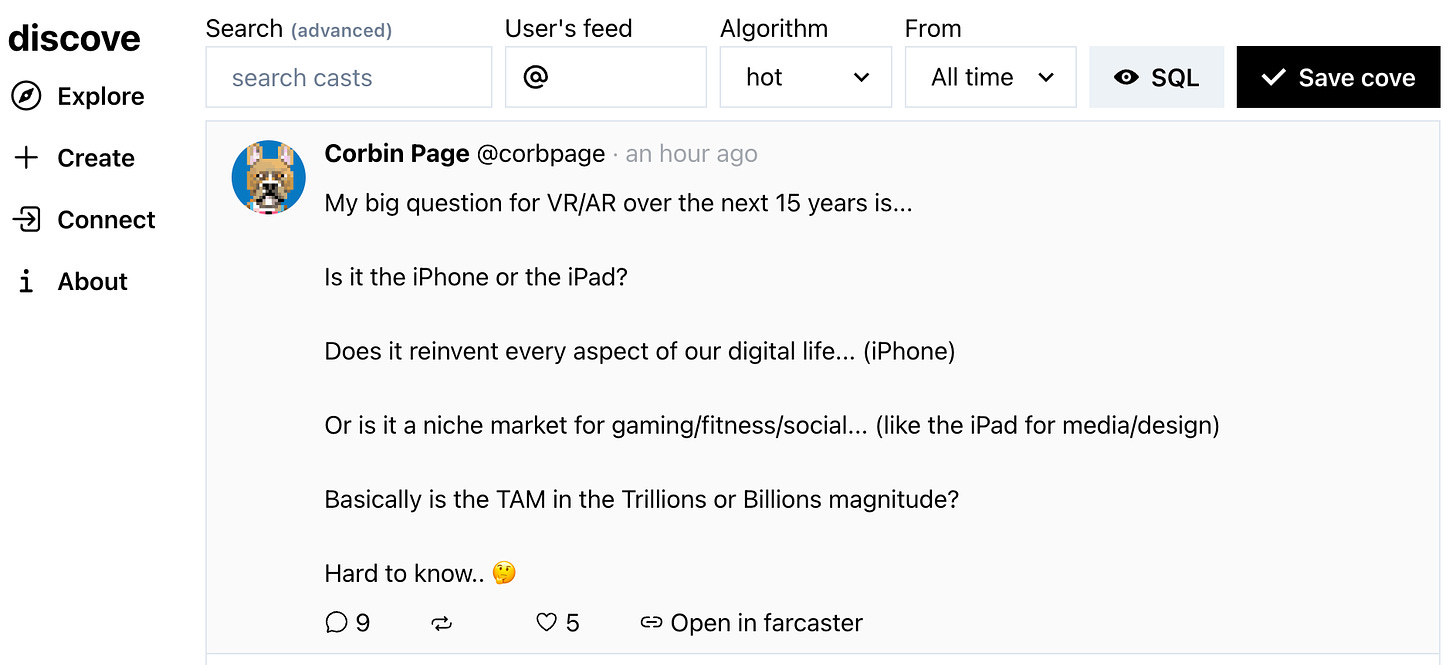
There’s already many applications built on Farcaster. Here’s a snippet (above) of discove one of the applications. There’s already lot’s of different approaches to the application layer. If you’re interested in checking them out, take a look at Alertcaster, Fardrop or Launchcaster, or having a look at the Farcaster ecosystem here: https://www.farcaster.xyz/ecosystem
So how does Farcaster work?
They first leverage the security of Ethereum to store Identities on-chain in smart contracts, the address that controls the Identity can then be used to sign off-chain messages on it’s behalf. This off-chain infrastructure is Farcasters own, always on – user controlled servers called ‘Hubs’. These hubs are used to validate, store, and replicate signed messages. This data is stored off chain due to it being expensive to store on most L1’s and L2’s.
With this system Farcaster enables a deeper focus on the application layer. Applications are programmes people use to interact with the Farcaster network, meaning users can switch between applications anytime to what best suites their needs. These applications can vary in complexity, some may only publish new messages and view messages published by others. While other apps may index the data and enable search, algorithmic feeds, and spam detection. These features of which are difficult or expensive to perform on the Hub itself.
This is another project you’ve probably heard of before – Lens Protocol, let’s dive in.
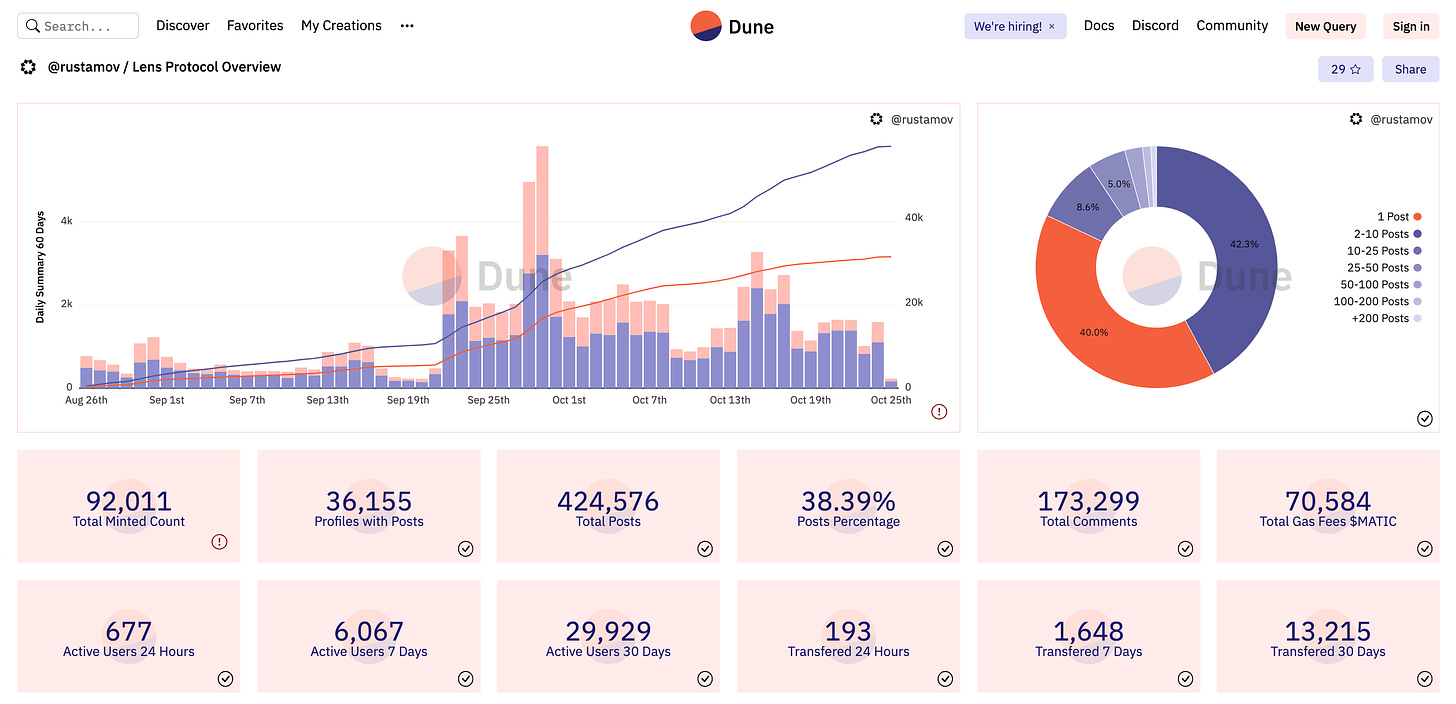
Lens has seen the biggest growth amongst all the protocols we’ll discuss in this article. Given that Lens mostly relies on NFTs, we can see from the dashboard above that there’s been 92,011 NFT Profiles minted, with 424,576 posts, 173,299 comments across all of these. We can also see that there’s 677 active users in the last 24 hours.
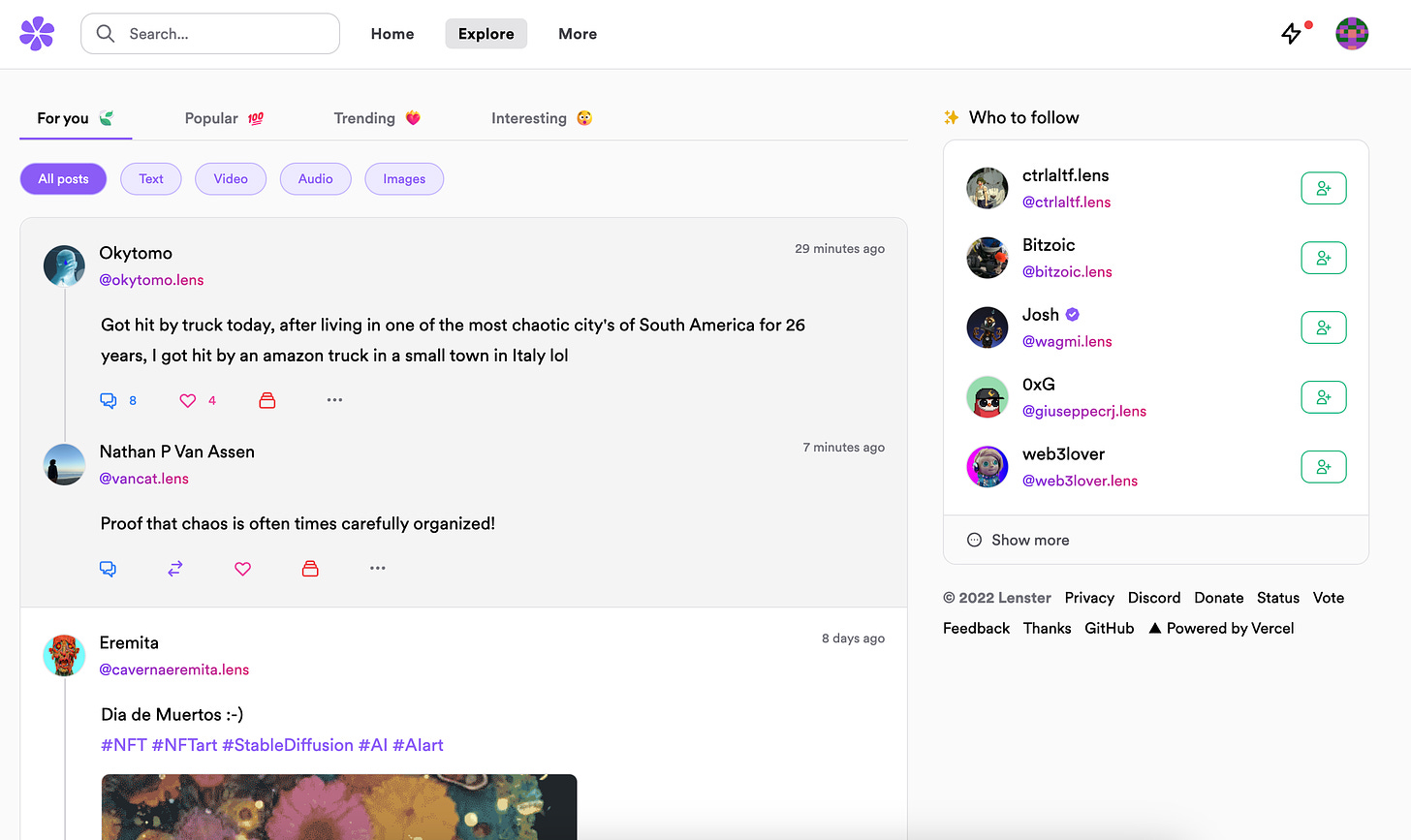
These stats are not surprising as some of the applications built on top are looking pretty slick, check out Lenster (below), similar Twitter, it even has filters for Popular, Trending and Interesting categories.
Although the stats from both Lens and Farcaster are decent, they don’t come close to that of Twitter. Which means we have a long way to go in order to achieve Twitters magnitude of network effect.
Looking into the Lens protocol itself – the protocol relies on Polygon NFT’s, more specifically the Lens Profile NFT, ownership of this gives the user control over their content. The cool thing about the Profile NFTs is that it allows you to post Publications. Publications come in three variations; Posts, Comments and Mirrors (shares). Additionally, Profile NFTs contain a FollowModule.
This module allows different accounts to be issued Follow NFTs in order to record their relationship to the main profile on-chain. It’s worth noting that Publications are NOT NFT’s. And the data that these Publications contain, can be stored on either a decentralized protocol such as IPFS, Arweave or a centralized storage provider like AWS S3. With this architecture, any applications can plug into Lens Protocol, and any user can bring their Profile to any application built on top of Lens.
Now Let’s take a look at CyberConnect, which is a bit more of a “meta” play, allowing anyone to develop their own social graphic for their specific application
CyberConnect protocol stores and manage users’ social data such as profiles, posts, and content in a decentralized manner. A cool benefit of CyberConnect is that users can publish their data in NFT format on a chosen blockchain for monetization purposes. CyberConnect relies on their own Social Data Network and Interest Graph Engine.
The Social Data Network comprises of their Data Infrastructure and Smart Contract Protocol. Their Data Infrastructure achieve’s data sovereignty through the use of cryptographic key pairs, storing said data via nodes on the network.
The Interest Graph Engine aggregates on-chain and off-chain data related to an identity and its activities. CyberConnect is an example of the Protocol layer, enabling developers to build social experiences such as Link3.
Link3 is built on top of CyberConnect, and is a Web3 native event planner. With Link3 events, users can now easily join the top events in Web3, as they own and create their verifiable identities through community participation. A cool feature of Link3 are these profile pages as seen above, we can think of this as a Web3 Linktree but with additional features.
The social category in on-chain identity is one to watch out for sure. The applications and protocols are real, usage is picking up and interest is starting to buzz. While there are still major network effects to overcome from traditional players like Twitter, this sector will be particularly exciting by the time the next bull run comes around. However, I think the bigger opportunity that still exists is the unique apps that will be possible yet never imagined with open source social graphs. It’s a new power that hasn’t fully been tapped into.
Anyways, that’s a wrap for this article. Look out for the next one covering the next major categories when it comes to on-chain identity!
Read More: kermankohli.substack.com











 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  USDC
USDC  Cardano
Cardano  Dogecoin
Dogecoin  TRON
TRON  Lido Staked Ether
Lido Staked Ether  Pi Network
Pi Network  Wrapped Bitcoin
Wrapped Bitcoin  Chainlink
Chainlink  LEO Token
LEO Token  Stellar
Stellar  USDS
USDS  Wrapped stETH
Wrapped stETH  Hedera
Hedera  Avalanche
Avalanche  Shiba Inu
Shiba Inu  Sui
Sui  Toncoin
Toncoin  Litecoin
Litecoin  Bitcoin Cash
Bitcoin Cash  Polkadot
Polkadot  MANTRA
MANTRA  Ethena USDe
Ethena USDe  WETH
WETH  Bitget Token
Bitget Token  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Hyperliquid
Hyperliquid  WhiteBIT Coin
WhiteBIT Coin  Wrapped eETH
Wrapped eETH  Monero
Monero  Uniswap
Uniswap  sUSDS
sUSDS  Dai
Dai  NEAR Protocol
NEAR Protocol  Aptos
Aptos  Pepe
Pepe  Ethereum Classic
Ethereum Classic  OKB
OKB  Ondo
Ondo  Internet Computer
Internet Computer  Coinbase Wrapped BTC
Coinbase Wrapped BTC  Aave
Aave  Gate
Gate  Mantle
Mantle  Official Trump
Official Trump