SaaS in a hybrid work environment
Change in the work environment brings changes to technology as well. Companies are opting for Software-as-a-Service (SaaS) as their primary mode of communication and productivity while working remotely.
The hybrid business model is a critical part of the distributed enterprise structure, and SaaS is an ideal fit for such an ecosystem. Organizations can benefit from SaaS in various ways.
- Reduced time to benefit: In the case of the SaaS model, the software application is already installed and configured. One needs to provide the server for an instance in cloud, and in couple of hours, the application is ready for use. This cuts down the time for installation and configuration.
- Cost savings: This model can reduce cost since it resides in a shared or multitenant environment. The hardware and software license costs are lower here than in the traditional model.
- Scalability: SaaS solutions reside in cloud environments that are scalable and are integrated with other SaaS offerings.
- Ease of use: SaaS offerings come with built-in best practices and samples, making them user-friendly and easy to use.
- Improve productivity and collaboration: SaaS can be used anytime, anywhere since it is cloud-based, thereby increasing employee productivity. This allows small and midsize businesses (SMBs) to invest more in hybrid work arrangements and to hire remote employees.
SaaS applications are changing the way we work as more and more organizations move their mission-critical data to the cloud. As per a Cloud Security Alliance (CSA) report, 89% of organizations host sensitive data in the cloud, and 67% store data in the public cloud.
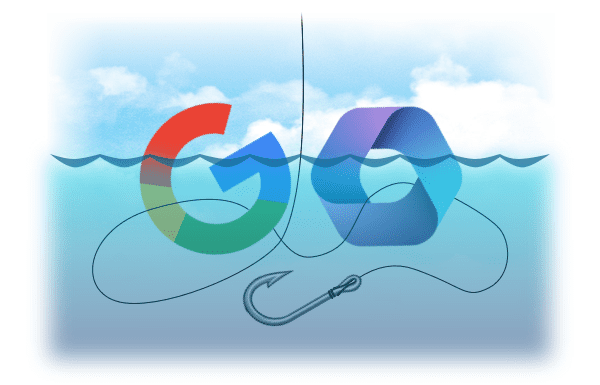
This transformation has catapulted the popularity of Microsoft and Google as SaaS offerings: Microsoft 365 is the leading Office suite technologies platform, which recently surpassed Google Apps in market share. Together Microsoft 365 and Google represent more than 94% of the market.
SaaS data in danger
With sensitive data stored in these cloud environments, there is a dire need for proper security. Organizations are found unprepared for ransomware attacks on their data stored in SaaS platforms. SaaS data was the target of 51% of ransomware attacks in the last 12 months. Ransomware attacks have a good success ratio against SaaS data (52%) compared to on-prem data centers (46%) and public cloud Infrastructure-as-a-Service (42%). These attacks are increasingly successful at encrypting SaaS data; only 50% of victims were able to fully recover SaaS data, compared to an 82% recovery rate for attacks against on-prem infrastructure.
To wreak havoc, ransomware requires a threat vector to gain access to the targeted systems and data. Two of the most common attack vectors (phishing and remote desktop protocol compromise) involve targeting end users/employees to gain access to the targeted credentials.
- Phishing: The majority of the ransomware gets delivered via phishing email campaigns. Phishing emerged as the top threat vector in 2021, according to an IBM report. Legitimate-looking emails are used here to trick employees into clicking on malicious URLs or opening an attachment containing malware. The URL then redirects the individual to a malicious site that triggers ransomware download. In the case of attachments, standard file formats like Word, PDF, Excel and ZIP are used to make it look less suspicious.
- Remote desktop protocol (RDP) compromise: Cybercriminals can also deploy ransomware via RDP, a communications protocol that enables IT admins to gain access to systems. Due to the rise in hybrid work culture, millions of RDP servers are exposed to the internet. Much of the credit (or, in this case, discredit) goes to weak password policies and misconfigured endpoint security. Hence, RDP serves as an easy entry point for the bad actors. They use port scanners to explore the web for systems with exposed ports. Once identified, the bad actors crack the login credentials with brute-force attacks and then log in as an admin.
How do they get your credentials? They phish you!
Attackers depend on manipulating human behavior to trick unsuspecting victims into revealing their credentials. These bad actors are opportunistic, ruthless and crafty. They engineer their mode of operation in ever-changing ways to bypass security implementations. 90% of all cyberattacks involve some form of social engineering.
Rather than hacking an organization’s networks and systems, cybercriminals can exploit human nature to carry out their nefarious act. They patiently wait for at least one individual from an organization to fall for the phishing lures planted carefully. All it takes is just one wrong move to breach an organization’s security perimeter and get hold of credentials.
Here are some of the ways cybercriminals attempted to phish Microsoft 365 environments:
Impersonating government agencies
U.S. government contractors get targeted with higher-quality lures and better-crafted documents in these ongoing phishing campaigns. The lure here is a request for bids for lucrative government projects. Once clicked, the malicious URL redirects to pages that are clones of legitimate federal agency portals. Threat actors associated with this campaign have been expanding their targeting scope, spoofing the likes of the Department of Transportation and the Department of Commerce.
Telltale signs in the older version of attached PDFs, which would have given away the ploy, are now carefully replaced with a simplified version that is smaller in size and features prominent logos and a link to the phishing page. A Captcha Challenge step is added on the page that dupes visitors into entering their Microsoft 365 account credentials to ensure bot inputs are not inserted.
Subverting multifactor authentication (MFA) via business email compromise (BEC) attacks
This phishing campaign targets CEOs and CFOs and exploits a Microsoft 365 productivity suite flaw. Consequently, hackers can pose as senior executives and send fraudulent invoices and financial requests.
This is a business email compromise (BEC) attack and combines high-end spear phishing with an adversary-in-the-middle (AiTM) attack, allowing hackers to bypass the multifactor authentication (MFA).
A phishing email is sent to a senior executive, which looks like a legitimate document from DocuSign and contains a malicious link. The visitor gets redirected to a fake Microsoft 365 login page after clicking the link. Once credentials are entered, the hackers can get access to it. A proxy server between the client and the real Microsoft server is implemented to bypass the MFA. As a result, hackers can intercept a valid cookie session and obtain access to monitor accounts and emails.
Carefully crafted campaign with multiple layers lending to its supposed credibility
This newly observed phishing campaign neutralizes one of the most popular anti-phishing techniques. It is designed to steal Microsoft 365 usernames and credentials via several malicious redirects.
In the series of open redirects, there’s a provision to take the victim to a malicious Google ReCAPTCHA verification page, and from there, to a fake Microsoft 365 sign-in page. Once the victim shares credentials on the page, it doesn’t end there. To add an extra layer of legitimacy to the entire episode, the victim is redirected to another fake page alleged to be Sophos.
One of the common methods to avoid falling for phishing lures is hovering the cursor over the link to have a look at the URL in question. However, this method is ineffective here, as the malicious actors behind the campaign have set up open redirects using a legitimate service.
The attackers have gone to similar lengths when it comes to attacking and compromising Google accounts and domains. These include:
Abusing Google Forms
Earlier this year, the bad actors were found abusing Google Forms for credentials and data exfiltration. In this sort of rudimentary phishing attack, hackers persuade victims to enter their credentials into a form designed to look like a login page. This happens in spite of many Google Forms warning users not to enter their passwords. These legitimate-looking forms often are tied to malicious spam campaigns. Malicious Windows applications also leveraged web requests to Google Forms pages to exfiltrate data from computers.
Spoofing legitimate companies via Gmail’s SMTP relay service
Since April 2022, attackers are exploiting Gmail’s SMTP relay service to carry out phishing attacks. Using the SMTP relay service, attackers can impersonate legitimate companies, thus making the emails look authentic. As such a malicious email appears to be from a legitimate company and domain, it easily bypasses Gmail’s spam filter and ends up in users’ inboxes.
Protecting your SaaS data from phishing attacks with Spanning 360
One single solution is ineffective in combating today’s advanced phishing attacks. That’s why organizations are opting for a defense-in-depth (layered defense) approach. It uses multiple controls in series to protect systems and data from potential threats. Under this framework, even if the attackers successfully penetrate through one layer, they will be thwarted by a subsequent layer. The layering of defense provides multiple redundancies in the event when systems and data are compromised.
Multiple layers of comprehensive email security are needed to safeguard your SaaS data from sophisticated phishing attacks. With Spanning 360, you get an end-to-end protection solution for Microsoft 365 and Google Workspace, with advanced capabilities to help prevent, anticipate and mitigate account compromise and data loss. It comes with three layers of phishing defense powered by patented AI technology that monitors communication patterns between people, devices and networks to spot untrustworthy emails. Integrated Dark Web Monitoring is another feature of Spanning 360 that provides continuous search, analysis and monitoring of the dark web for any compromised or stolen Microsoft 365 and Google Workspace credentials. In the event of data loss or corruption, easily restore clean version of files with Spanning Backup’s point-in-time restore capabilities.
Want to see Spanning live in action? Get a demo today!
Read More: news.google.com







 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  Dogecoin
Dogecoin  USDC
USDC  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  TRON
TRON  Avalanche
Avalanche  Sui
Sui  Wrapped stETH
Wrapped stETH  Toncoin
Toncoin  Chainlink
Chainlink  Shiba Inu
Shiba Inu  Stellar
Stellar  Wrapped Bitcoin
Wrapped Bitcoin  Hedera
Hedera  Polkadot
Polkadot  WETH
WETH  Bitcoin Cash
Bitcoin Cash  LEO Token
LEO Token  Uniswap
Uniswap  Litecoin
Litecoin  Pepe
Pepe  Hyperliquid
Hyperliquid  Wrapped eETH
Wrapped eETH  NEAR Protocol
NEAR Protocol  Ethena USDe
Ethena USDe  USDS
USDS  Internet Computer
Internet Computer  Aptos
Aptos  Aave
Aave  Mantle
Mantle  POL (ex-MATIC)
POL (ex-MATIC)  Cronos
Cronos  Render
Render  Ethereum Classic
Ethereum Classic  Bittensor
Bittensor  MANTRA
MANTRA  Monero
Monero  Tokenize Xchange
Tokenize Xchange  Artificial Superintelligence Alliance
Artificial Superintelligence Alliance  Dai
Dai  Virtuals Protocol
Virtuals Protocol  Arbitrum
Arbitrum