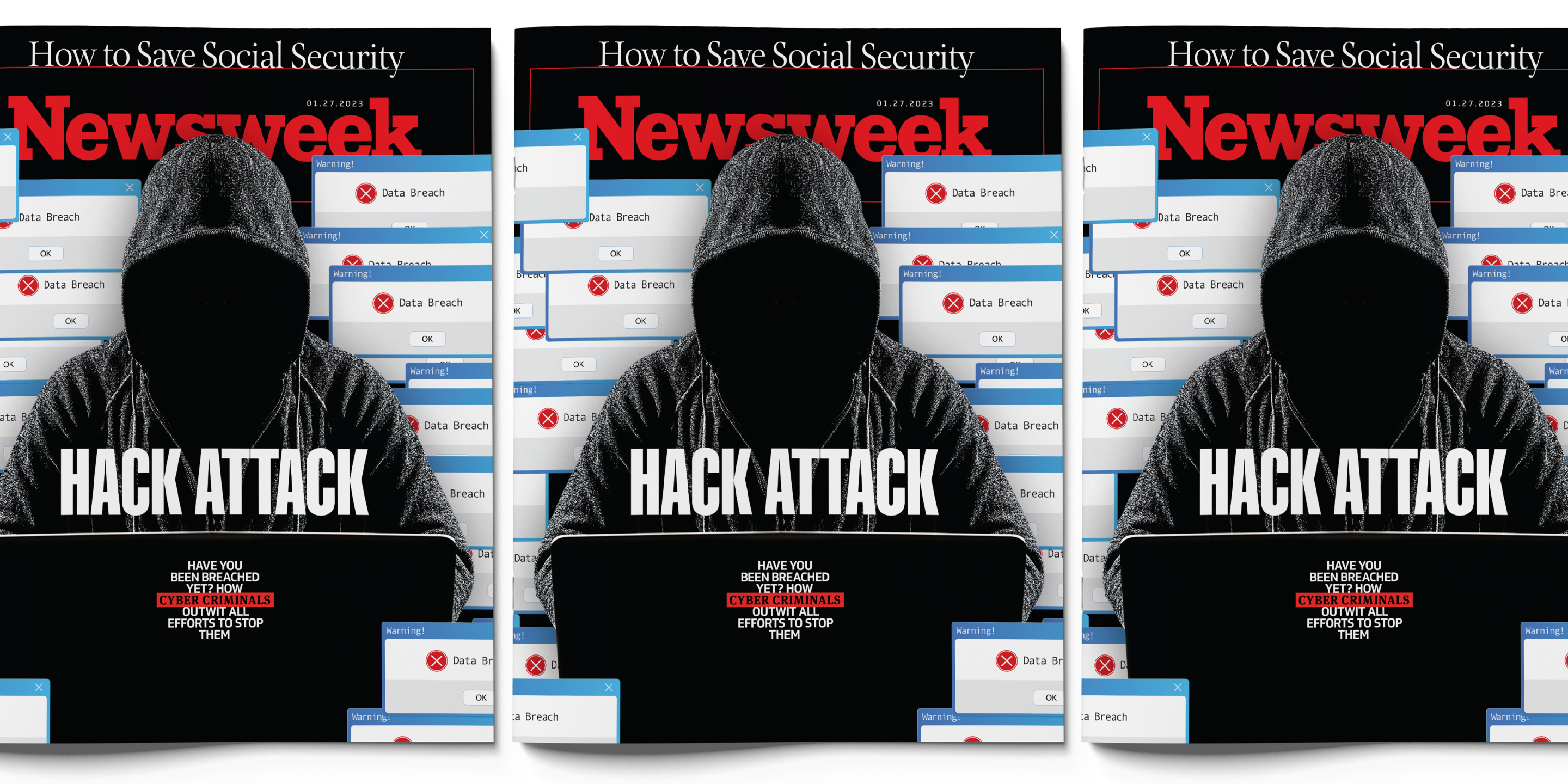
On the morning of January 11, the Federal Aviation Administration halted all airline takeoffs in the U.S. because of a glitch in a software system critical to flight safety. “There is no evidence of a cyberattack at this point,” said the White House press secretary. But would officials know it if it were? And would they disclose it to the public?
Those are fair questions, given that in 2015 it took the FAA two months to disclose that hackers had planted malware in one of its computer networks. The federal government keeps tight wraps on what it knows about threats to American businesses and individuals.

If hackers did indeed attack the FAA, it would be business as usual in the world of cybersecurity. On the same day, according to research firm Cybersecurity Ventures, hackers posted more than 120,000 records stolen from the San Francisco Bay Area transit system’s police department, took down the websites of eight major Danish banks, including the central bank, and broke into military and government agencies in several Southeast Asian and European countries. They also hijacked the cloud-computing platforms of Microsoft and Salesforce, making off with millions of dollars worth of untraceable cryptocurrency.
That’s just on January 11. Every day of the year, hackers unleash a stream of major attacks against government agencies, companies and individuals. Last year, they took down emergency services, threatened regional power grids, disrupted patient care at major hospitals, brought trains to a halt, took over radio stations to sow panic among listeners with a fake crisis, set off air-raid alerts and attacked U.S. nuclear scientists. So far this year, hackers broke into the communications firm Slack and stole email addresses of more than 200 million Twitter users.
More than 70 million Americans are hit by cybercrimes every year, according to computer security research firm Purplesec, often leaving people defrauded, spied on or publicly humiliated by having private photos and other information published online. More than two-thirds of small businesses have been victimized by hackers at least once. Some experts believe that just about every large organization and government agency has been breached—that’s how enormous and constant cyberattacks have become. Last year, 22 billion personal and business records were exposed in hacks on U.S. companies, according to a study by security consultancy Flashpoint—and that doesn’t include breaches that were unidentified or unreported, which may well represent the majority of hacks.
As bad as it’s been, it’s getting worse. According to security firms that track attacks, the number of breaches, which had been growing by 15 percent a year, jumped by 38 percent in 2022.
There are many reasons why hackers seem to have the upper hand. For one, they’ve become institutionalized, with backers such as Russia, China and other nations providing shelter and funding to massive ranks of hackers in their countries. The targets are also growing more numerous, as billions of people hook up tens of billions of new gadgets to the internet, each providing an entry point to computer networks. And powerful new hacker tricks and tools—some of them powered by artificial intelligence—are springing up almost daily on the black market.

Courtesy of Check Point
As a result, hackers now have the ability to flood computers everywhere with an endless stream of potent attacks. “We’re talking about trillions of events,” says Mark Ostrowski, who heads engineering for major computer security vendor Check Point Software Technologies.
Most people are vaguely aware that computer crime is rife but have no idea how severe the problem has become and how quickly it’s expanding. Many attacks are kept under wraps, keeping the problems out of sight. Even CEOs of major companies sometimes lack a clear idea what their industries are facing. Last year, the newly created U.S. Office of the National Cyber Director held a forum to brief CEOs on some classified intelligence on cyber threats. The CEOs’ reaction: “Complete shock,” says principal deputy national cyber director Kemba Walden.
The U.S. government, with all its cyber warfare prowess, has failed to protect its own citizens and businesses, for whom the prospect of relief is nowhere in sight. “It’s a cyber pandemic,” Ostrowski says, “and it’s going to get worse before it gets better.”
Deadly Threats
It wasn’t supposed to be like this. Two decades ago, experts wrote off hacking as temporary growing pains of the nascent internet. Security professionals were slowly but surely getting hacking under control with improved tools and practices. “The vast majority of hackers do not have the necessary skills and knowledge” to do much damage, said a 2004 report from the U.S. Institute of Peace, a federal bipartisan think tank, and “the ones who do, generally do not seek to wreak havoc.”
Where have these assurances left us today? “We have a saying in the industry,” says Marc Rivero, a senior security researcher with cybersecurity software firm Kaspersky Labs. “Ninety-five percent of organizations have been breached, and the other five percent just don’t know they were breached.” The bottom line, agree most experts, is that no computer, or any device or machine with a computer chip, can today be considered fully safe.
Security professionals, forever playing catch-up, seem helpless to get the problem under control. “The criminals are two steps ahead of us,” says David Maimon, director of the Evidence-based Cybersecurity Research Group at Georgia State University as well as a researcher with the Hebrew University in Jerusalem. “If they want in, they’ll be in.”
The event that most epitomizes the degree to which hackers can run the table was the 2020 attack on SolarWinds, a software firm. Hackers breached the company’s computer networks and planted malware—software that does bad things—in its software products. When clients downloaded SolarWind’s product updates, they got the malware, too. “When the software is released, all the computers that use it are immediately compromised,” says Kaspersky’s Rivero.
The SolarWinds attack gave hackers access to the computers of so many companies and even government agencies that the hack is considered by many experts to be the most damaging ever. (Of course, there may be other damaging attacks that were never made public.) Security experts worry that infiltrating software companies as a way to get at their clients is a new strategy that will spawn copycat crimes. “That’s going to be a key target for criminals in 2023, for sure,” says Rivero.
The SolarWinds incident is generally attributed to hackers supported by Russian intelligence agencies. Russia has become a bustling center of hackerdom, in part because the Russian government uses hacking extensively for purposes of warfare. That has been the case in its Ukraine invasion, as well as for spying on and otherwise harming the U.S. and other countries it considers hostile. China and North Korea, too, and to a lesser extent Iran, are known to have extensive state-supported hacking capabilities for disrupting enemies, as does the U.S.
In some cases these countries are working with sophisticated cyber criminals as well as cultivating their own hacker armies. Russia has been especially tolerant of its thriving ranks of cyber criminals, as long as they focus on targets in other countries. “I don’t think there’s evidence of Putin directing criminals to commit ransomware attacks, but there hasn’t been much interest there in handing over criminals who do,” says Troy Hunt, a security consultant who founded the prominent personal-data-breach-tracking website “Have I Been Pwned?” .
These developments are raising the concerns about potential attacks on power grids, air traffic control systems and food supply chains, among other targets, potentially with severe consequences. “Targets include nuclear power plants, medical devices, autonomous vehicles and industrial control systems,” says Mordechai Guri, who heads research and development at Ben Gurion University’s Cyber Security Research Center in Israel. “In extreme cases, they could cause deaths. You can imagine the effect of a cyberattack on autonomous vehicles.”
Guri is referring to the self-driving cars that are already being tested in several cities and states in the U.S. and elsewhere. Many medical devices, from pacemakers to powerful MRI machines, have some form of network connectivity, as do some traffic lights, elevators and many other devices and machines that could in theory be commandeered to deadly effect. Hacker-inflicted disruptions to the energy grid could kill thousands if they happened during periods of extreme cold or heat.
Computer hacks have already begun to prove deadly. In 2020, hackers shut down computer systems at Düsseldorf University Hospital in Germany, disrupting emergency care, among other functions. In the ensuing chaos a critically ill patient died before the hospital could arrange for a transfer. Many other institutions have had close calls after being hit by hackers, including Toronto’s Hospital for Sick Children, Canada’s largest pediatric hospital, which last year lost its ability to access medical tests and imaging or use its phones in a hacker attack. When Long Island’s Suffolk County government offices were hit, the automated 911 system went down, forcing emergency personnel to take information down by hand, and leaving them unable to track callers’ locations.

Scott Eisen/Getty
A long list of attacks with potentially deadly consequences have taken place in the past two years. Air-raid sirens went off in Israel last year when hackers breached the nation’s public-defense system. A month later hackers took over Ukrainian radio stations to falsely report that President Volodymyr Zelenskyy was mortally stricken. In 2021 hackers took over computers at a water-treatment facility in Florida and contaminated the water supply, a life-threatening attack that was barely discovered in time to prevent disaster. A few months later hackers forced the shutdown of the largest oil pipeline in the U.S. for a week until the pipeline operator paid the hackers $4.4 million to back off. Last year more than 100 attacks were launched against various elements of the U.S. power grid.
It’s no coincidence the attacks are getting more numerous and scarier. In addition to gaining support from Russia and other hostile nations, hackers worldwide are becoming better organized and equipped, often functioning more like an interconnected global industry than scattered bands of criminals. “There is now an elaborate, deep and sophisticated hacking supply chain,” notes Georgia State’s Maimon. “Some write malware, some distribute it, some use it, some sell the results.”

Sean Gallup/Getty
Most of the transactions happen over the Darknet, the portion of the internet that is encrypted to hide its websites from search engines and anyone without the right passwords. Hacking groups with names like Fancy Bear, Conti and Killnet advertise on the Darknet to sell their ill-gotten data and access, recruit other hackers, buy tools and inside information, and sell their services as cyber mercenaries. “Some hackers will buy affiliation with a group for $50,000 or more, plus a cut of the revenues,” says Maimon. Transactions typically happen via Bitcoin, which makes them difficult to trace.
Business analytics firm Thoughtlab reports that the number of breaches has been increasing at an annual rate of 15 percent, but new data from Check Point indicates the growth rate jumped to 38 percent in 2022. About 200 ransomware attacks are reported each month in the U.S. on average,
according to data from Secureworks, which sells computer security tools. Among the more prominent victims of ransomware hacks reported in December alone: the California Department of Finance; the Little Rock, Arkansas, school system; the British Guardian newspaper; and hospitals in Maryland, Texas and Florida. Many more such attacks likely go unreported because victims choose not to go public.
A Plague of Cybercrime
While the specter of attacks that can kill people and disrupt society may make more ordinary, financially oriented cybercrime seem tame in comparison, the sheer size of the problem is becoming an economic nightmare that’s starting to affect lives of people around the world.
Hackers, for instance, are becoming adept at intercepting corporate email and changing invoices so that money is sent to their own accounts. “Those attacks are a fast-growing threat,” says Mike McLellan, Secureworks director of intelligence. “It’s costing companies billions.”
And while attacks on companies are the most potentially lucrative, hackers are also all too happy to pick our individual pockets, one by one, usually by tricking us into giving them the passwords to our bank, credit card and other financial accounts. Their routines are growing increasingly ingenious and convincing, notes Adam Wandt, vice chair for technology at John Jay College of Criminal Justice. Wandt describes how a friend of his was fooled by a piece of malware into calling a phony customer support number for the financial service he uses; the ensuing “help” drained his life savings. “Even sophisticated people get tripped up all the time by these schemes,” says Wandt. “I know people with doctorates in criminal fraud who get taken in.”
In the past, computer security experts at least didn’t have to worry about hackers getting into some of the world’s most potentially dangerous equipment, including nuclear power plants and missile systems. That’s because these systems, along with computers critical to national defense, are usually “air-gapped”—that is, they lack any sort of wireless or wired connection to the rest of the world. Only someone standing next to these machines could have access to them.

Adrian Bretscher/Getty
Guri and colleagues, in a paper published in December in Cornell University’s ArXiv, demonstrated how hackers could use electromagnetic waves not unlike radio signals to alter the programming of air-gapped machines. The technique is highly complex, and requires physical access at some earlier point—presumably on the part of a bribed or blackmailed insider—to implant malware simply by briefly inserting a USB thumb drive, for example. But those requirements aren’t beyond the capabilities of hostile governments. And as experts at Kaspersky Labs have noted, hackers might be able to direct tiny drones close enough to a target machine to help set up an attack.
To be sure, security experts are continually coming up with new tools and techniques for detecting and stopping cyberattacks. But these advances never stop hackers for long. “People ask if we’re winning the war against hackers, but it’s like asking if we’re winning the war against fingernails,” says security expert Hunt. “You can cut them back, but they just keep growing.”
Hackers have easy access to software tools with names like Doppelpaymer, CobaltStrike and Ninja that can automatically sniff out weaknesses in computer systems and sneak in to plant “back doors” that let the hackers do their dirty work without being detected. When security experts foil these tools, hackers immediately come up with new types of attack. “No matter how much innovation we see on the security side, the hackers are always racing to figure out ways to compromise it,” says John Jay College’s Wandt. “We keep seeing new, outside-the-box attacks that catch us by surprise. Today there isn’t a single piece of security software that hackers can’t get around.”
Georgia State’s Maimon warns that while cyber criminals are getting better at their tricks, computer users aren’t getting better at seeing through them. Maimon ran a study in which a group of users were trained on how to avoid falling for phishing schemes, and then two weeks later he sent them all a phony email note with a suspect link that could have easily led to malware. A quarter of the people in the study clicked on it. Meanwhile, hackers only need to wring a click from one person to infiltrate an organization of thousands.

Carolyn Pruden Richardson
Part of the problem, says Maimon, is that there is a serious shortage of highly skilled people on the security side. Cybersecurity Ventures reports that the number of unfilled computer security positions rose from one million in 2013 to 3.5 million in 2021, and is expected to stay high through 2025. That leaves badly understaffed security groups facing off against millions of hackers around the world, many of whom are no less than brilliant. One reason for the imbalance is pay. “The good guys can’t make as much as the bad guys,” says Maimon.
Machine learning, a form of artificial intelligence (AI), is starting to lend a hand to the security side, notes Check Point’s Ostrowski. “It’s our only hope for keeping up with the trillions of attacks we see,” he says.
There’s just one problem, he adds: Hackers are turning to machine learning tools, too. “We’re already seeing an AI arms race in computer security,” he says. Check Point recently demonstrated how hackers might already be enlisting “ChatGPT,” a popular, publicly accessible AI system that can understand plain-English requests in order to come up with everything from slick-sounding essays to fully functioning software code. Check Point’s researchers showed the program can also create multiple types of new hacking attacks such as malware and phishing emails.
The U.S. government is trying to step up its game in foiling hackers by, among other things, creating the Office of the National Cyber Director in the White House in 2021. So far, the office’s main activity has been holding the executive forums, such as one recently aimed at the electric vehicle industry. Principal deputy director Walden wouldn’t provide details of the threats, exactly how the agency will help bolster defenses against them, or how much money will be spent on the effort. But she noted the agency would be issuing a public report soon, and is planning to develop a safe-computing information campaign. “We want to provide that education piece for everyone from preschoolers to grandmothers,” she says.
Follow the Money
Hackers have an enormous incentive to keep at it: Stolen information is valuable. That’s why Australia has suffered two major hacking attacks since September, one involving the theft of the drivers-license-related personal data of half the nation’s drivers, the other lifting the health records of 40 percent of the population. “That means hackers know about millions of people’s drug and alcohol dependence, abortions and sexually-transmitted diseases, among other highly personal information,” says Hunt.
The hackers didn’t do it out of sheer maliciousness. They did it because they can make an enormous fortune selling it—to other criminals, for example, who can use the personal information to pull off identity theft, blackmail and other crimes. Or they can threaten to publish it as part of a ransomware play. “The basic idea is to get the data first, and then figure out later what it might be worth,” says Secureworks’ McLellan.

Stephen Morton/Bloomberg/Getty
Although the value of stolen data depends on a number of factors, Secureworks has tracked the going prices on the Darknet for some of the data stolen in recent months around the world: a bundle of 2,000 U.S. tax returns goes for $3,000; a batch of credit card data goes for $20 to $100 per card; 487 million WhatsApp phone numbers fetches $16,500; and passwords to the computer systems of a major U.S. corporation go for $2,000. McLellan adds that if stolen information includes proprietary technical details on a high-tech product, then Russia, China and other less-scrupulous national governments are likely to be eager buyers—if they didn’t sponsor the hack in the first place.
Pretty much anything that’s kept on a computer can be up for grabs to the right buyer. In December two men in New York were arrested on charges of conspiring with Russian hackers to break into the taxi dispatch system at Kennedy Airport, allowing them to sell front-of-the-line access to taxi drivers for $10 a pop. They collected as much as $10,000 before they were nabbed.
Meanwhile, the range of hackable targets is rapidly expanding daily, especially thanks to the growing number of devices that are getting hooked up to wireless networks. As more and more everyday devices from door locks to cars to cameras become internet-connected, they can be weaponized to track, rob or cause physical damage. “We all have an average of seven devices hooked up to the Internet, and it’s more all the time,” says Maimon. Home security cameras, smart watches, car information systems—all have suffered prominent hacks, and far more hacks of these devices have likely been left undiscovered or unreported.
As the number of connected devices grows, so will the number of hacks, and the types of information that can be stolen. One new vulnerability that came to light in December was the discovery by a researcher that Google Home smart speakers can be taken over by hackers not only to listen into conversations, but also to gain remote access to smart door locks and other home devices that are networked with the speakers. “If it’s online, it’s vulnerable,” says Maiamon.
More interconnected gadgets generates more data that needs to be stored remotely in the cloud—vast forests of computer servers operated by
Amazon, Google, Microsoft and other tech giants. While those companies provide access to advanced security tools that can protect that data, the software developers who make use of the cloud don’t always properly deploy them, leaving enormous stores of aggregated data less than fully protected and ripe for hackers. “Thanks to the cloud, it’s never been easier to quickly build applications and screw them up so they’re not safe,” says Hunt.

Courtesy of Troy Hunt
In the end, contends Hunt, the only safe piece of data today is data that isn’t kept on any computer, anywhere. “We need to start minimizing our digital footprints,” he says. “Every time you sign up for a service, they want your phone number and birthdate. We have to stop giving away that information.”
The public is not up in arms over the high risk of hacking because most people aren’t aware of how large those risks have become and how little can be done to reduce them. Experts and the government can continue to plug the new security holes that hackers will continue to find, as they have for decades, and to try to track hackers down and bring them to justice. In most cases, this is a lost cause. For one thing, it is difficult to trace attacks back through a vast global forest of internet connections. And Russian, Chinese and millions of other hackers are well protected from international law enforcement. “It’s the nature of the internet that the attackers can be anywhere,” says Hunt. “The chances of recourse are none.”
And the government and experts can and will keep telling people to have better passwords that they never share, to be more careful about what they click on in email notes, and to use extra sign-in precautions such as those that require facial or fingerprint recognition or send a verification note to your phone or a special “authenticator” app. But most people don’t want the inconvenience of these precautions. When companies or government agencies try to force people to take them, people often find ways around them. “You end up with ‘shadow IT,’ like when people use Gmail instead of company email to avoid the inconvenience of the extra protections,” says Ostrowski.
The route to full computer security may in the end be less about plugging holes in our defenses, and more about unplugging. But if that’s the case, then the picture isn’t likely to improve any time soon. How many of us are really ready to swear off the online world and smart devices? Not many, according to analytics firm Statista, which reports that the number of devices connected to the Internet, currently at just under 15 billion, is expected to double over the next eight years. The future is looking more and more chaotic and dangerous.

Read More: news.google.com








 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  USDC
USDC  Dogecoin
Dogecoin  Cardano
Cardano  TRON
TRON  Lido Staked Ether
Lido Staked Ether  Wrapped Bitcoin
Wrapped Bitcoin  Sui
Sui  Wrapped stETH
Wrapped stETH  Chainlink
Chainlink  Avalanche
Avalanche  Hyperliquid
Hyperliquid  Stellar
Stellar  Shiba Inu
Shiba Inu  LEO Token
LEO Token  Hedera
Hedera  Bitcoin Cash
Bitcoin Cash  Toncoin
Toncoin  Litecoin
Litecoin  Polkadot
Polkadot  USDS
USDS  WETH
WETH  Monero
Monero  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Wrapped eETH
Wrapped eETH  Bitget Token
Bitget Token  Pepe
Pepe  Pi Network
Pi Network  Ethena USDe
Ethena USDe  Coinbase Wrapped BTC
Coinbase Wrapped BTC  WhiteBIT Coin
WhiteBIT Coin  Bittensor
Bittensor  Dai
Dai  Uniswap
Uniswap  Aave
Aave  NEAR Protocol
NEAR Protocol  Aptos
Aptos  OKB
OKB  Jito Staked SOL
Jito Staked SOL  Ondo
Ondo  BlackRock USD Institutional Digital Liquidity Fund
BlackRock USD Institutional Digital Liquidity Fund  Cronos
Cronos  Ethereum Classic
Ethereum Classic  Internet Computer
Internet Computer