Welcome to the Future
So you’ve decided to dive into web3, dApps, and the fascinating world of degenerate gamblers and obstinate builders of the internet’s future.
Or, perhaps you want to join in on the fun and experiment with new dApps, but are afraid of the numerous ways you see people losing money by falling for scams and malicious platforms. You’re not tech savvy and believe you’ll be an ideal victim for the next scam.
Fortunately for you, I’m sharing the fundamentals of online security when using crypto, DeFi, and web3.
This article will take you through the steps you should take in order to be safer as you learn and progress on web3. I’ll assume you’re using Google Chrome and Metamask, which are the most popular tools right now.
Beginner: Being Your Own Bank
The advantage of web3 logistics is that you set it once and don’t have to worry about it again. You’ll gain confidence to go further in this new space if you secure your accounts and funds. So, let’s start with the fundamentals and how to secure everything.
1. Enable Two-Factor Authentication on All Accounts
2FA, or Two Factor Authentication, will save you a lot of trouble if hacks occur on the centralized apps you use. When creating any account, go straight to settings and activate it. Here’s an example with a Twitter account, after going to “Settings”:
Step 1:
Step 2:
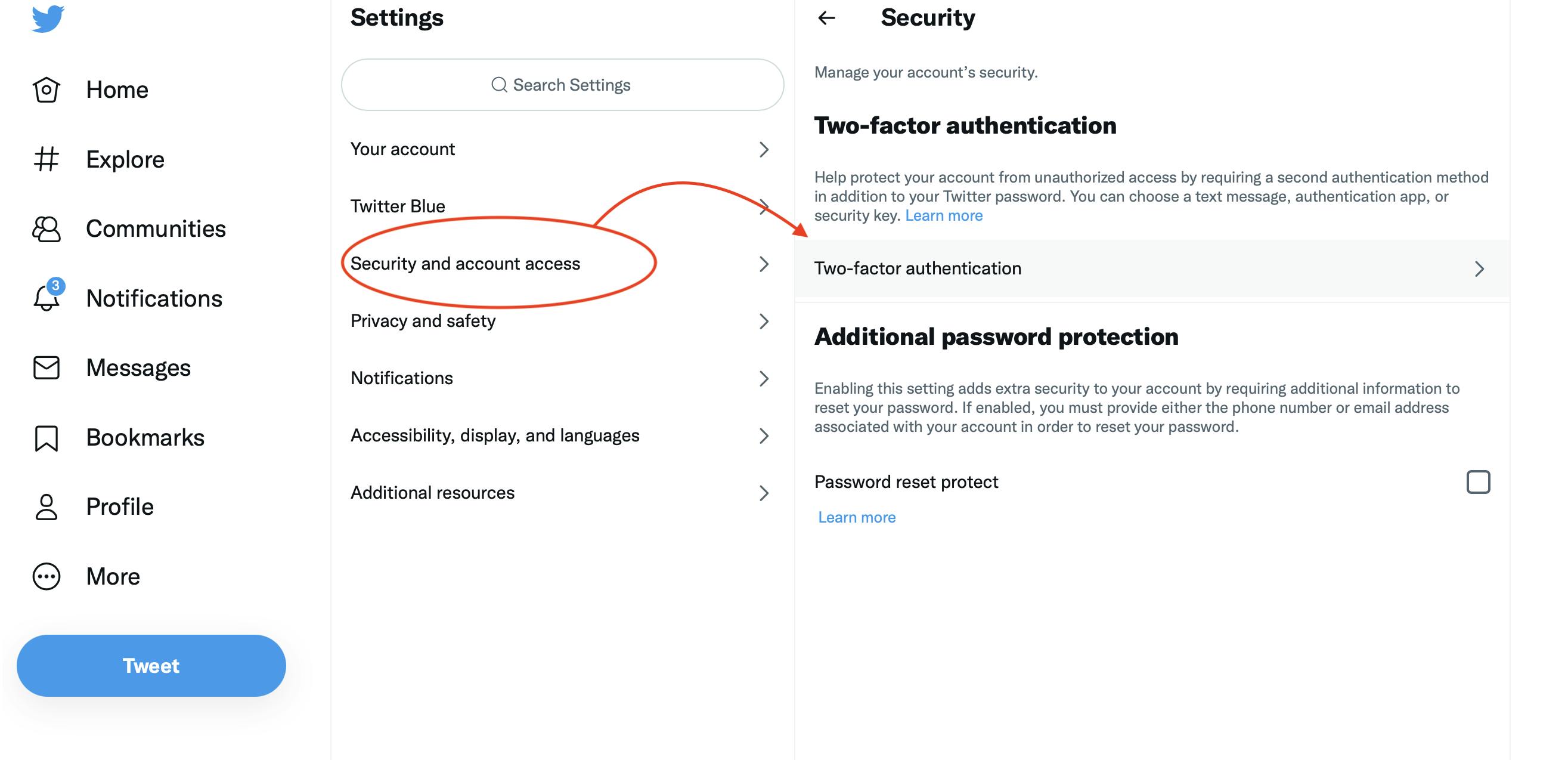
It’s critical that you don’t use a phone number as a 2FA measure, as SIM card swapping is a common practice among hackers nowadays. And yes, crypto users are also targeted.
Instead, you can use a 2FA app, which will generate a code for each time slot and allow you to log in after entering the code. The most popular 2FA apps are Google Authenticator and Authy.
Step 3:
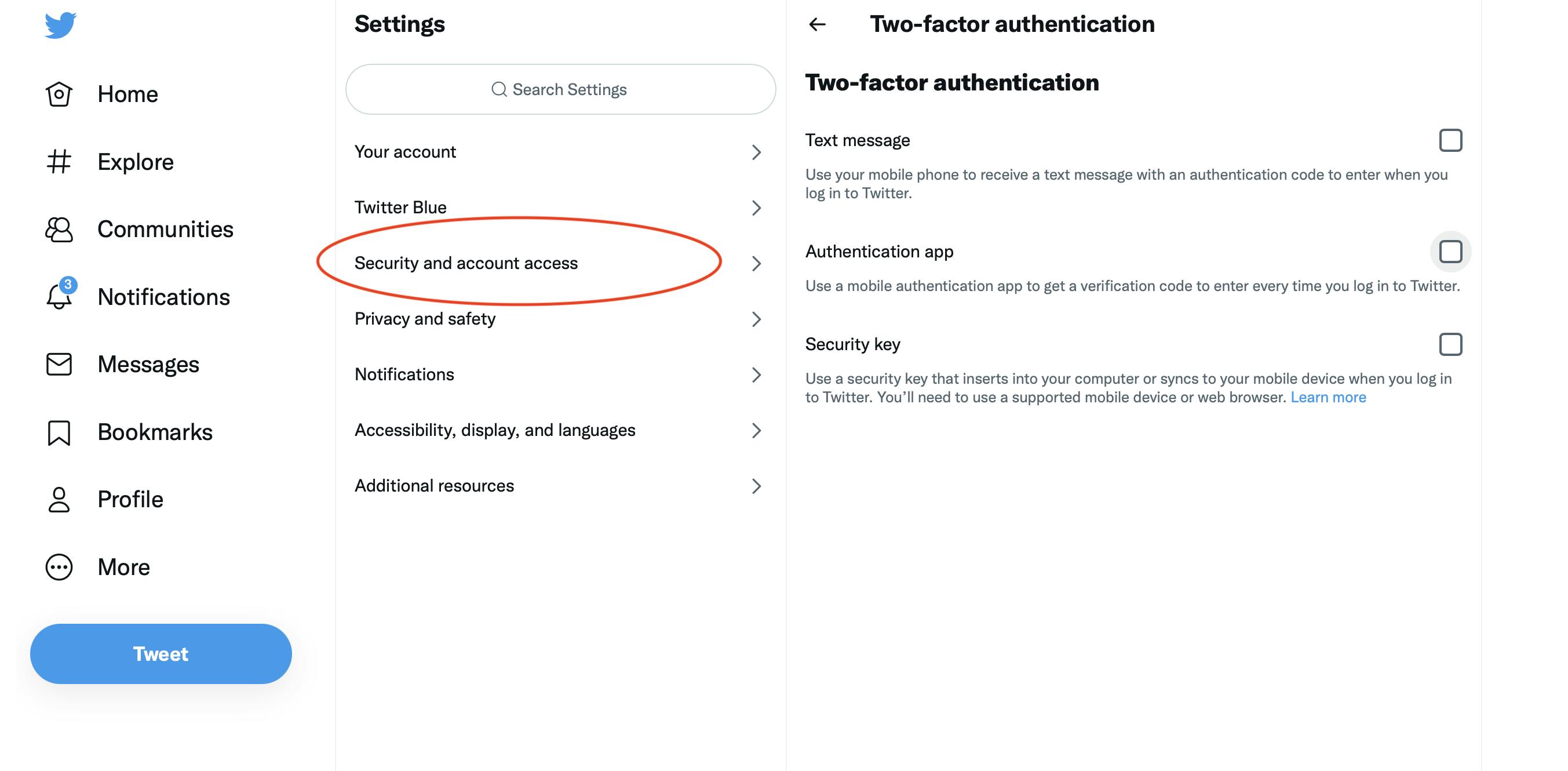
The first thing you should do is protect your CEX account, which is where you buy and sell crypto for fiat.
The next thing you should do is secure your social and forum accounts, where you discuss cryptocurrency, to avoid being hacked and granting access to potential victims, especially if you have a large audience.
Why Protect Your Social Accounts?
Having your social media accounts hacked can also disqualify you from projects in which you may be interested. For example, if your address is whitelisted to mint a project, the hacker can change it and replace it with his.
Hacked social media accounts can also be purchased for pennies on the internet. There’s a thriving market for verified Twitter accounts with large followings. Some specialized crypto websites will sell your rank on some servers (which usually grants you privileges such as airdrops, token allocations, or being on a private sale).
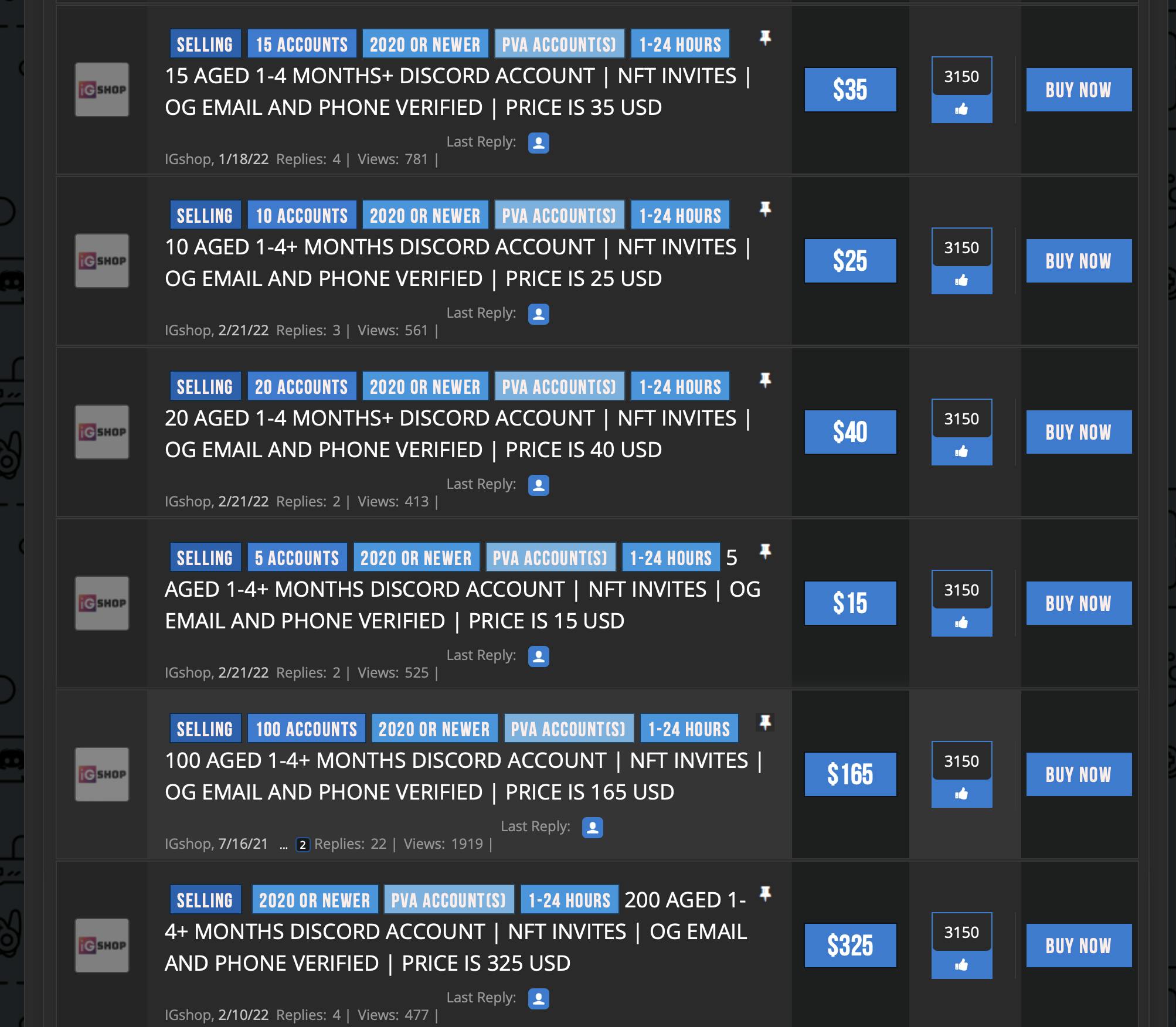
Typically, verified Twitter accounts are purchased by scammers or NFT projects with the intent of rug pulling (vanishing with people’s coins after minting), or even cloning sites for successful projects. The scammers also need a fake account on a centralized exchange (CEX) to cash out the money.
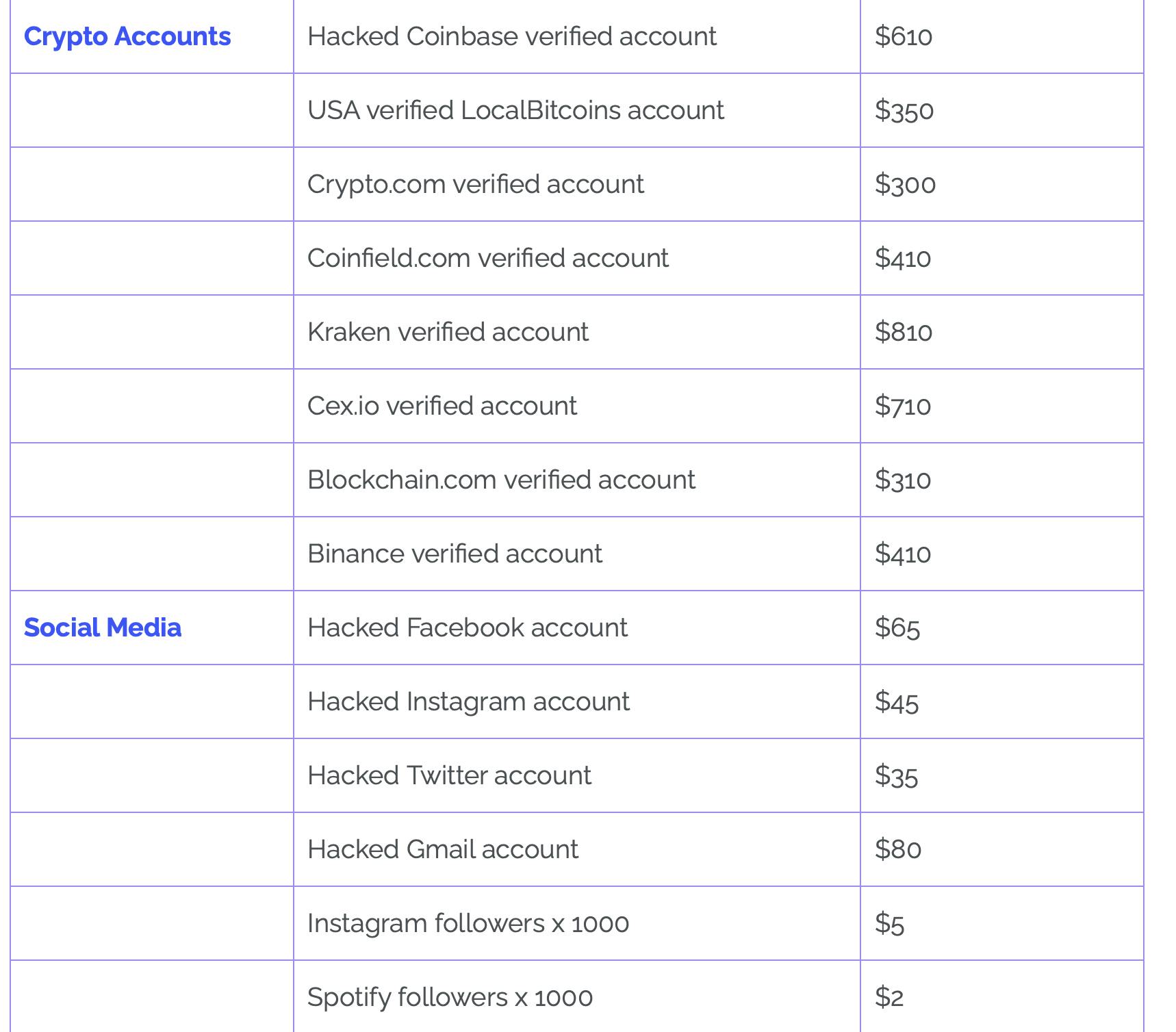
This screenshot is from this report. You can…
Read More: web3.hashnode.com









 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  Dogecoin
Dogecoin  USDC
USDC  Lido Staked Ether
Lido Staked Ether  Cardano
Cardano  TRON
TRON  Avalanche
Avalanche  Chainlink
Chainlink  Wrapped stETH
Wrapped stETH  Toncoin
Toncoin  Wrapped Bitcoin
Wrapped Bitcoin  Shiba Inu
Shiba Inu  Sui
Sui  Stellar
Stellar  Polkadot
Polkadot  Hedera
Hedera  Hyperliquid
Hyperliquid  WETH
WETH  Bitcoin Cash
Bitcoin Cash  LEO Token
LEO Token  Uniswap
Uniswap  Litecoin
Litecoin  Pepe
Pepe  Wrapped eETH
Wrapped eETH  NEAR Protocol
NEAR Protocol  Ethena USDe
Ethena USDe  USDS
USDS  Aptos
Aptos  Internet Computer
Internet Computer  Aave
Aave  Cronos
Cronos  POL (ex-MATIC)
POL (ex-MATIC)  Mantle
Mantle  Ethereum Classic
Ethereum Classic  Render
Render  WhiteBIT Coin
WhiteBIT Coin  MANTRA
MANTRA  Monero
Monero  Dai
Dai  Bittensor
Bittensor  Artificial Superintelligence Alliance
Artificial Superintelligence Alliance  Arbitrum
Arbitrum  Ethena
Ethena