
Cloudflare has defended against a distributed denial-of-service (DDoS) attack that reached a new record of 71 million requests per second. The record-breaking DDoS attack surpassed the previously reported record of 46 million requests per second in June 2022 by 35%.
The attacks took place over the weekend and peaked at approximately 50 million to 70 million requests per second. These HTTP/2-based attacks targeted Cloudflare-protected websites and were traced back to over 30,000 IP addresses.
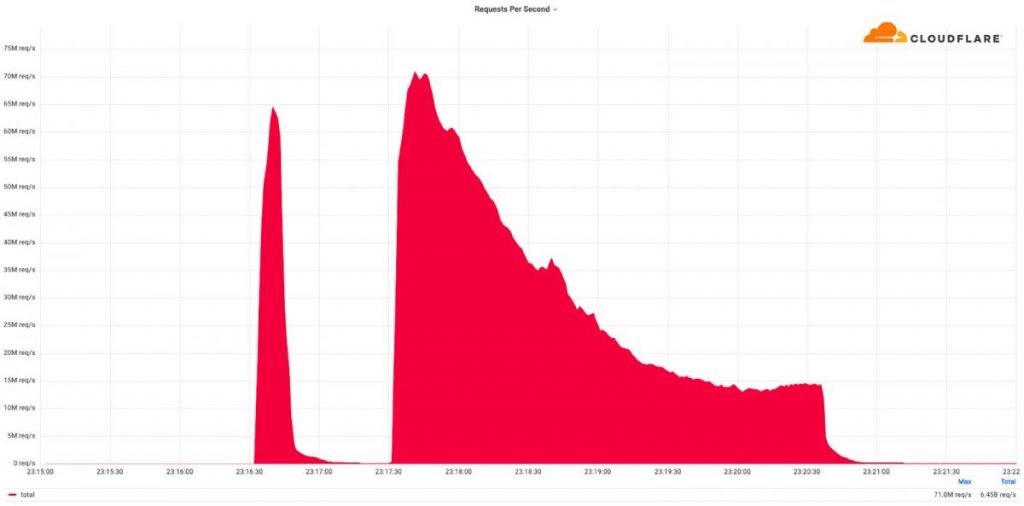
The DDoS-affected sites included a popular gaming provider, cryptocurrency companies, hosting providers, and cloud computing platforms. According to Cloudflare, “the attacks originated from numerous cloud providers.”
“Over the past year, we’ve seen more attacks originate from cloud computing providers,”
the company added.
Cloudflare will offer a free botnet threat feed to service providers with autonomous systems. The feed will provide threat intelligence about providers’ own IP spaces and the origins of attacks.
The internet infrastructure company claims that DDoS attacks have been increasing in size, sophistication, and frequency. In its latest DDoS threat report, Cloudflare observed a 79% yearly increase in HTTP DDoS attacks, a 67% QoQ rise in volumetric attacks exceeding 100 Gbps, and an 87% QoQ increase in attacks lasting over three hours.
The intention behind a DDoS attack is to impede the normal flow of traffic to a targeted network, server, or service by flooding the system or its surrounding infrastructure in a malicious effort. The objective of such cyberattacks is to disable internet properties and restrict user access. They are particularly potent against sites lacking adequate protection, requiring only minimal resources and expenses for the perpetrators to launch.
Related posts:
Read More: mpost.io









 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  USDC
USDC  Dogecoin
Dogecoin  TRON
TRON  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  Wrapped Bitcoin
Wrapped Bitcoin  Hyperliquid
Hyperliquid  Sui
Sui  Wrapped stETH
Wrapped stETH  Chainlink
Chainlink  Avalanche
Avalanche  LEO Token
LEO Token  Stellar
Stellar  Bitcoin Cash
Bitcoin Cash  Toncoin
Toncoin  Shiba Inu
Shiba Inu  Hedera
Hedera  USDS
USDS  Litecoin
Litecoin  WETH
WETH  Wrapped eETH
Wrapped eETH  Monero
Monero  Polkadot
Polkadot  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Ethena USDe
Ethena USDe  Bitget Token
Bitget Token  Pepe
Pepe  Coinbase Wrapped BTC
Coinbase Wrapped BTC  Pi Network
Pi Network  WhiteBIT Coin
WhiteBIT Coin  Aave
Aave  Uniswap
Uniswap  Dai
Dai  Ethena Staked USDe
Ethena Staked USDe  Bittensor
Bittensor  OKB
OKB  Aptos
Aptos  Internet Computer
Internet Computer  Cronos
Cronos  NEAR Protocol
NEAR Protocol  BlackRock USD Institutional Digital Liquidity Fund
BlackRock USD Institutional Digital Liquidity Fund  Jito Staked SOL
Jito Staked SOL  Ondo
Ondo  sUSDS
sUSDS