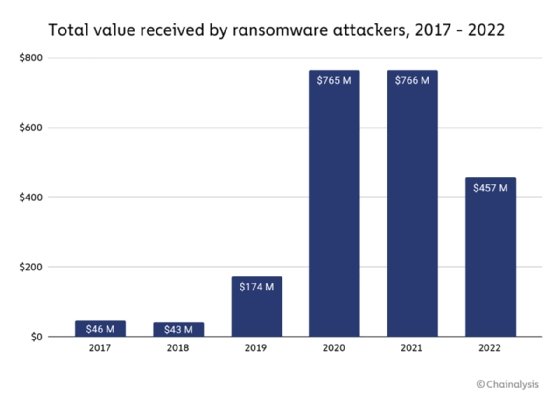
Ransomware payments dropped from $766 million in 2021 to $457 million in 2022, according to new research from blockchain research firm Chainalysis.
The research, published as a blog post Thursday, is dedicated to the revenue threat actors gained via ransomware payments last year. In addition to the 2022 and 2021 figures, Chainalysis said it tracked $765 million in ransomware payments in 2020, $174 million in 2019, and just over $40 million in both 2018 and 2017.
The blog post conceded that “the true totals are much higher” due to cryptocurrency addresses that are yet to be identified. Even with this caveat, Chainalysis argued that not only are ransomware payments significantly down, but they are down because fewer victims are paying the ransom rather than fewer attacks occurring.
Jackie Koven, Chainalysis head of cyber intelligence, told TechTarget Editorial that the vast majority of the $457 million figure is made up of bitcoin, with some Ethereum transfers included as well. She said that the ransomware ecosystem is “dominated” by bitcoin, and that Chainalysis believes privacy coins like Monero make up a small percentage of ransomware payments.
“One reason is [privacy coins] aren’t as liquid as Bitcoin and other cryptocurrencies,” Koven said. “Especially now that many exchanges have delisted privacy coins given regulatory guidance, they’re increasingly impractical. Cryptocurrency is only useful if you can buy and sell goods and services or cash out into fiat, and that is much more difficult with privacy coins. As we acknowledge in the report, our data does improve over time and we expect our ransomware figures to grow in subsequent reports, but have no reason to believe it will reach levels seen in 2020 and 2021.”
Chainalysis’ report provided two primary reasons for the sharp decline. First, the blockchain firm referenced the threat of sanctions, providing a September 2021 advisory by the U.S. Department of the Treasury’s Office of Foreign Assets Control as an example. The second reason is cyber insurance firms demanding steeper cyber-readiness requirements from customers before agreeing to insure them.
The firm also referenced data from incident response firm Coveware, which claimed that only 41% of victims paid the ransom in 2022 — down from 50% in 2021 and 70% in 2020.
Another notable data point from Chainalysis’ report involved the average life span of a ransomware strain. According to the firm, the average ransomware strain remained active for 70 days in 2022, down from 153 days in 2021 and 265 in 2020.
This is “likely related to ransomware attackers’ efforts to obfuscate their activity, as many attackers are working with multiple strains,” the post read.
The research claimed that despite this turnover, and despite the constant appearance of new strains, “the actual number of individuals who make up the ransomware ecosystem is likely quite small.” This is due in large part to affiliate overlap, Chainalysis said.
“Most ransomware strains function on the ransomware-as-a-service (RaaS) model, in which the developers of a ransomware strain allow other cybercriminals, known as affiliates, to use the administrator’s malware to carry out attacks in exchange for a small, fixed cut of the proceeds,” the blog post read. “However, we’ve seen time and time again that many affiliates carry out attacks for several different strains. So, while dozens of ransomware strains may technically have been active throughout 2022, many of the attacks attributed to those strains were likely carried out by the same affiliates.”
Chainalysis compared the ransomware ecosystem to the ride-sharing industry, pointing out that even though a driver might work with Uber, Lyft and other providers, it’s still just a single driver behind the wheel.
Alexander Culafi is a writer, journalist and podcaster based in Boston.
Read More: news.google.com









 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  USDC
USDC  Dogecoin
Dogecoin  Cardano
Cardano  TRON
TRON  Lido Staked Ether
Lido Staked Ether  Sui
Sui  Wrapped Bitcoin
Wrapped Bitcoin  Chainlink
Chainlink  Avalanche
Avalanche  Wrapped stETH
Wrapped stETH  Stellar
Stellar  Shiba Inu
Shiba Inu  Hedera
Hedera  Hyperliquid
Hyperliquid  Toncoin
Toncoin  Bitcoin Cash
Bitcoin Cash  USDS
USDS  Litecoin
Litecoin  LEO Token
LEO Token  Polkadot
Polkadot  WETH
WETH  Monero
Monero  Wrapped eETH
Wrapped eETH  Bitget Token
Bitget Token  Pepe
Pepe  Pi Network
Pi Network  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Coinbase Wrapped BTC
Coinbase Wrapped BTC  Ethena USDe
Ethena USDe  WhiteBIT Coin
WhiteBIT Coin  Uniswap
Uniswap  Bittensor
Bittensor  NEAR Protocol
NEAR Protocol  Aptos
Aptos  Dai
Dai  Aave
Aave  Ondo
Ondo  OKB
OKB  Ethereum Classic
Ethereum Classic  sUSDS
sUSDS  Internet Computer
Internet Computer  Cronos
Cronos  BlackRock USD Institutional Digital Liquidity Fund
BlackRock USD Institutional Digital Liquidity Fund  Official Trump
Official Trump