Cross-chain decentralized finance (DeFi) protocol Rubic was compromised, resulting in funds stored in its user’s addresses being siphoned out and transferred to the hackers.
On Dec. 25, Rubic protocol announced that one of its routing contracts was compromised and all contracts would be stopped until the situation is fully understood. The announcement read:
The protocol’s creators also advised their users to revoke contract authorization through the revoke.cash tool. A Twitter thread by blockchain cybersecurity firm PeckShield explains that a vulnerability in the Rubic protocol led to a loss of $1.41 million worth of funds directly from the wallets that authorized its smart contracts.
The exploiter address received the funds from the Uniswap decentralized exchange (DEX) in transactions involving the USD Coin (USDC) stablecoin. PeckShied explained that the hack was made possible due to mistakenly adding USDC into supported routers. Furthermore, “a lack of validation in ruterCallNative” also allowed malicious contract use.
A quick smart contract analysis with the help of chatGPT suggests that the ruterCallNative function contains numerous potential vulnerabilities, including invalidated input for the “_params” and “_data” parameters. These could allow an attacker to pass malicious input that could result in incorrect or unintended behaviour.
Furthermore, the “_gateway” parameter passed to the function is unrestricted, potentially allowing an attacker to create a contract and have it executed by the RubicProxy contract.
Indeed, the attacker deployed a custom smart contract that was used in the attack. The decoded bytecode shows the 337 lines of code that allowed the attacker to perform the attack as efficiently as possible.
The hacker’s address received first a 1,161.55 ethereum (ETH) transfer and another 26.88 ETH transfer, both from the Uniswap protocol siphoning out exclusively USDC and exchanging it for wrapped ethereum (WETH). All of this WETH was later sent to an on-chain mixer and sanctioned entity Tornado Cash to anonymize the ill-gotten funds.
On-chain analysis shows that $1.45 million worth of incoming transactions sent to the coin anonymization service originated from the hacker’s address — on a total incoming value for the service of about $2.9 million. In other words, about half of the assets sent to the mixer today were sent by the exploiter.
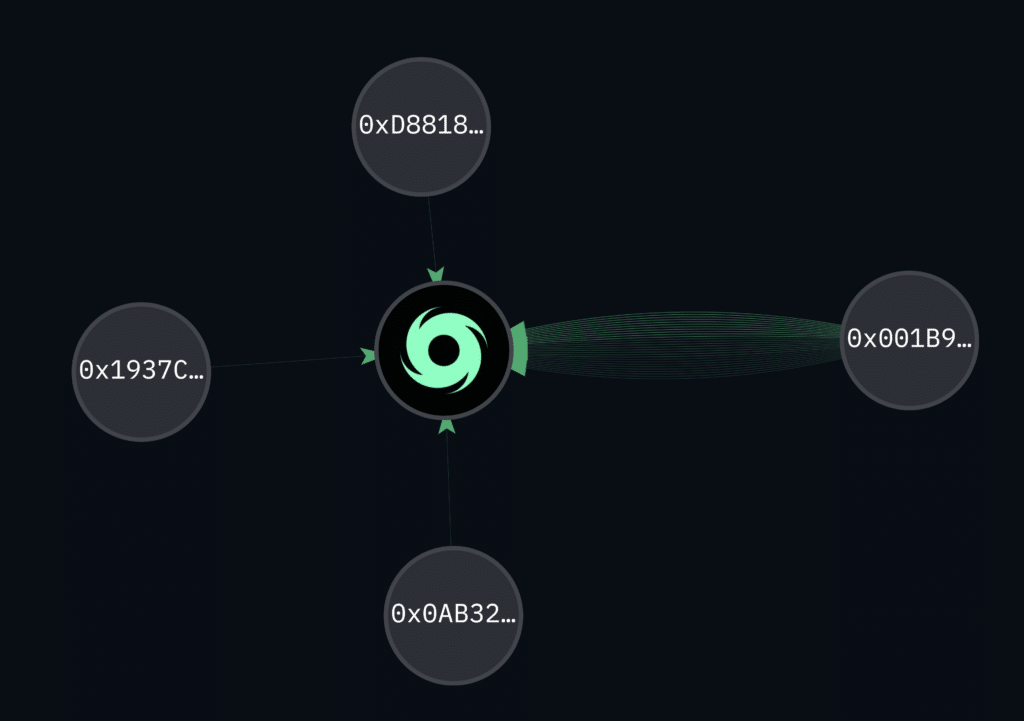
Despite the hacker’s funds being such a significant portion of the service’s incoming transaction volume, their anonymity is still substantial. The deposit may be among the $2 million withdrawals from Tornado Cash processed today or among the $174 million worth of assets still deposited in the smart contract.
Tornado Cash is a now-illegal DeFi protocol that allows users to perform anonymous transfers on the Ethereum blockchain. The protocol uses zero-knowledge proofs (ZK-proofs) to hide transactions’ input and output addresses. It is difficult for third parties to determine the identity of the parties involved in the transaction or the specific purpose of the transfer.
Tornado Cash is an open-source project built on top of the Ethereum blockchain and accessible to anyone with an Ethereum wallet. Users can interact with the Tornado Cash contract using their Ethereum wallet or a web interface still available through the decentralized hosting service InterPlanetary File System (IPFS). They can perform anonymous transfers of ETH or tokens compliant with the ERC-20 standard by sending their funds to the Tornado Cash contract and withdrawing them to a new address.
The news follows recent reports that North Korean hackers have stolen around $1.2 billion in cryptocurrency and other virtual assets over the past five years. Most of those hacks happened in 2021 alone.
Read More: crypto.news








 Bitcoin
Bitcoin  Ethereum
Ethereum  Tether
Tether  XRP
XRP  Solana
Solana  USDC
USDC  Dogecoin
Dogecoin  TRON
TRON  Cardano
Cardano  Lido Staked Ether
Lido Staked Ether  Wrapped Bitcoin
Wrapped Bitcoin  Sui
Sui  Wrapped stETH
Wrapped stETH  Hyperliquid
Hyperliquid  Chainlink
Chainlink  Avalanche
Avalanche  Stellar
Stellar  LEO Token
LEO Token  Toncoin
Toncoin  Bitcoin Cash
Bitcoin Cash  Shiba Inu
Shiba Inu  Hedera
Hedera  USDS
USDS  Litecoin
Litecoin  WETH
WETH  Wrapped eETH
Wrapped eETH  Polkadot
Polkadot  Monero
Monero  Binance Bridged USDT (BNB Smart Chain)
Binance Bridged USDT (BNB Smart Chain)  Bitget Token
Bitget Token  Pepe
Pepe  Ethena USDe
Ethena USDe  Pi Network
Pi Network  Coinbase Wrapped BTC
Coinbase Wrapped BTC  WhiteBIT Coin
WhiteBIT Coin  Dai
Dai  Uniswap
Uniswap  Aave
Aave  Bittensor
Bittensor  NEAR Protocol
NEAR Protocol  Aptos
Aptos  OKB
OKB  Jito Staked SOL
Jito Staked SOL  Ethena Staked USDe
Ethena Staked USDe  BlackRock USD Institutional Digital Liquidity Fund
BlackRock USD Institutional Digital Liquidity Fund  Tokenize Xchange
Tokenize Xchange  Cronos
Cronos  Ondo
Ondo  Internet Computer
Internet Computer